- Table of Contents
- Overview
- Web Application Security
- Operating System Security
- Network Security
- Knoppix - NSM
- Overview of Kerberos Authentication, Part 1
- Kerberos Implementation
- Kerberos Implementation, Part 2
- Kerberos Implementation, Part 3
- Kerberos Implementation, Part 4
- Kerberos Implementation, Part 5
- Kerberos Implementation, Part 6
- Kerberos Implementation, Part 7
- Kerberos Implementation, Part 8
- Network Attacks
- Remotely Owning Your Network
- How to Stay Anonymous Online
- Security Consideration for Remote Assistance
- Secure Remote Access with Radmin v2.2
- Secure Remote Administration Using Famatech’s Remote Administrator v3.0
- Secure, Remote Windows Mobile Development
- Securing your Windows Servers with GFI LANguard Network Security Scanner
- A Look Inside CORE IMPACT
- Owning Systems with CORE IMPACT
- What is a Firewall?
- Configuring Client-side SFTP to Secure Your File Transfers
- The Finer Details of SSH
- CSRF vs. AT&T: Your World Delivered - To Someone Else
- Security Analysis of a Scan to Desktop/PC Solution
- Exploiting Scan to PC/Desktop Applications
- SCADA and Security
- SCADA In-Security
- FTP, SFTP and FTP/S
- Authentication Proxies: Secure or Not?
- Hardening Your System
- Wireless Security
- Mobile Security
- Data Forensics
- Legal and Ethical Issues of Security
- Home User Security
- Additional Resources
- Job Security for the IT Security Industry
- A Biased Book Review: Chained Exploits: Advanced Hacking Attacks from Start to Finish
- Security of Mechanical Locks
- Information Security in Academics
- Holiday Security: Hackers Don’t Take Holidays
- Gary McGraw on Building Secure Software
- Gary McGraw on Exploiting Online Games
- A Student-Hacker Showdown at the Collegiate Cyber Defense Competition
- The Collegiate Cyber Defense Competition Year 3: Revenge of the Red Cell
- Questions from RSA 2007
- How to Steal 80,000 Identities in One Day

How to Stay Anonymous Online
Last updated Jan 1, 2004.
This section covers:
Disguising your identity online
Maintaining anonymity
NOTE
Portions of this article are adapted from the book "Windows .NET Server Security Handbook by Cyrus Peikari and Seth Fogie. Prentice Hall, 2001.
Overview
As a modern security consultant, there will be times when you need to go trolling in the computer underground in order to stay current on zero day exploits. However, this is best done anonymously, in order to avoid retaliation from hackers and script kiddies. For example, one of our InformIT authors was celebrated for being the first to track down, socially engineer, and document a notorious hacker crew that was using IRC bots to control thousands of slave computers used in DoS attacks. Unfortunately, he forgot to use anonymous proxies, so in retaliation his workplace was DoS'd offline! Here we show you how to remain anonymous online so that you can protect yourself.
Advanced users with an interest in security often subscribe to software vulnerability mailing lists such as Bugtraq. Bugtraq is the generic term for a large class of mailing lists that describe how to exploit (and how to fix) software applications by revealing their specific security weaknesses. There are currently several privately owned lists that use the name "Bugtraq." Symantec Corp. owns the best known of theres. Until now, the majority of Bugtraq lists have operated on the principle of full disclosure, which means that these weaknesses are announced publicly.
By keeping abreast of the most recently published exploits, you can often install patches on your system in time to prevent catastrophe. However, a list such as Bugtraq is limited in that it only lists publicly known vulnerabilites. In some situations, you may find that you also need access to unknown vulnerabilities as well. If this is the case, then your best source of knowledge is to go to the underground hackers themselves. Hackers often employ a technique known as camping, in which they keep an exploit secret for days until they can coordinate a massive strike. It is during this camped time, which is like the quiet before the storm, that you can extract the occult data.
Disclaimer
Using the techniques described in this section, you will often be able to uncover the most dangerous vulnerabilities 7 days or more before they are exploited. However, counterintelligence (spying) on the hacker underground is a time-consuming and potentially dangerous endeavor. We do not recommend using the procedures in this chapter unless you are an expert or working under the supervision of a law enforcement officer.
Examples of groups who might find it useful to have advance warning of vulnerabilities include the following sectors:
- Law enforcement
- Government
- Military
- Infrastructure
- Finance
- Security consultants
- Wargames contestants
Before proceeding, it is important to pause and carefully consider ethics. If you do happen to come across a camped exploit, it is your ethical and legal duty to promptly notify both law enforcement and the manufacturer of the targeted software product.
Cloaking your identity
When traversing the computer underground, it is imperative to maintain anonymity. If a hacker detects that your IP address is coming from a .gov or .mil domain, he is unlikely to give up the crown jewels. Similarly, if you leave a trail you could expose yourself to retaliation. This section will briefly describe how you can cloak yourself on the Internet.
Choosing an Alias
The most obvious step in masking your identity is to choose an alias, or fake screen name. A well-designed alias should engender trust in the hacker while providing no trace of its origin. As an example of a well-engineered alias, we will use the screen name "cornholio."
Using Anonymizers
When surfing the Internet, you leave a trail of information detritus that can be used to track you back to your workplace or home. Some of the information a hacker sees when you visit his website includes the following:
IP Address: The unique IP address that identifies you on the Internet. Your IP address is logged at almost every website and at the routers in between.
Browser Type and Operating System: For example, "Mozilla/4.0 (compatible; MSIE 5.5; Windows 98)" is what your computer may reveal to web sites. This information is useful for a hacker to launch browser-based attacks against you.
Referrer: The referrer is the web site that 'referred' or sent you to the web site that is pulling this information from your computer. This means that your path or route to any website could be monitored, which might reveal clues to your identity.
All of the above information is what shows up even if you have the highest security settings on your computer. This is because your computer automatically sends every site it visits a description of itself. For example, your computer may be shouting out the following information:
Accept: image/gif, image/x-xbitmap, image/jpeg, image/pjpeg, application/vnd.ms-powerpoint, application/vnd.ms-excel, application/msword, application/x-quickviewplus, */* Accept-Language: en-us Connection: Keep-Alive Host: privacy.net Referer: http://www.anonymizer.com/why.shtml User-Agent: Mozilla/4.0 (compatible; MSIE 5.5; Windows 98) Accept-Encoding: gzip, deflate
A quick way to cover your tracks is to use a web-based anonymizing front end such as that found at http://rewebber.de/ or at http://anonymizer.com/. However, such tools are limited and incomplete. In order to provide true anonymity, you will have to utilize anonymous proxies.
Anonymous Proxies
MultiProxy
A correctly configured anonymous proxy can help give you complete anonymity. http://multiproxy.org offers Windows proxy software as well as lists of anonymous proxies and excellent assistance in learning how to tune your system for anonymity.
As shown in Fig. 1, MultiProxy listens on port 8088 by default, so you will need to configure your browser to connect to Internet via proxy server at address 127.0.0.1 (localhost) and port 8088. You can change the port number from options dialog box. If you want other computers on your LAN (without Internet access) to connect to Internet through MultiProxy, you need to enter the actual IP address of the computer where MultiProxy has been installed (instead of 127.0.0.1). You can quickly find your Internet-connected computer's IP address by running ipconfig.exe at a command prompt (console).
Configuring MultiProxy
Clicking the Options tab in MultiProxy reveals three tabs, as shown in Fig. 2.
Under general options, select the following configuration:
Accept connections on port: 8088
Connect Via: Anonymous Proxies Only
Connect back to my computer to port #: 8081
You must next populate Multiproxy with a list of active anonymous proxies. Fortunately, http://www.multiproxy.org provides a fresh supply of regularly updated anonymous proxies.
Configuring Anonymous Browsing
Now that you have multiproxy configured, you must set your browser to utilize proxies. Depending on the browser type and version you are using, the settings will differ slightly.
Under your browser preferences, edit the "Proxies" information and make the following changes:
In the Address of proxy server to use, for HTTP enter 127.0.0.1 (Fig. 3)
In the Port field, enter 8088
Your browser is now configured for anonymous surfing.
TIP
Make sure to test your browser for anonymity before implementing it. Visit http://privacy.net/ for a quick online test of your anonymity.
Configuring IRC for Anonymity
Without IRC (Internet Relay Chat), you will not get very far into the hacker underground. IRC is the communication tool of choice for hackers. As an ethical infosec expert you will need to protect yourself when researching in the underground by cloaking your identity.
Installing MIRC
MIRC is a popular client for using IRC. The latest version is available from shareware download sites such as http://www.download.com.
After installing and starting MIRC, you will be able to connect to a hacker IRC server.
Once you are connected you should see a welcome message. You can then join a channel by typing /join #channelname at the prompt. Take care! You are now conversing live with fearsome and elite hackers, as shown in Fig. 5.
We may think that our identity is now safe, but in fact we have made a glaring error. We are running multiproxy with anonymous servers, but everyone in the chat room easily read our IP address. In retaliation for our faux pas we can now expect to be DoS-ed, spammed and Trojaned in every orifice of our network. How did this happen?
The answer lies in the fact that we need to integrate a SOCKS proxy to our HTTP anonymizer. The next segment will show you how to do this.
Socks2HTTP
Socks2HTTP is a software application that converts SOCKS v.5 requests into HTTP requests and tunnels them through an HTTP proxy. The SOCKS protocol allows programs to traverse firewalls on any port number and is used by many popular programs such as Napster, MSN Messenger, CRT (a telnet client) and many others.
However, many network administrators restrict firewall traversals to HTTP requests only, thus disabling SOCKS proxies. Socks2HTTP allows users to circumvent this by providing a miniature SOCKS server for the SOCKS client, allowing it to perform its connection through an HTTP proxy. Thus, it is a very handy application. Unfortunately, later versions are embedded with adware, so unless you are lucky enough to have an older version, be prepared to deal with that drawback. You can find the latest version of Socks2HTTP at http://www.totalrc.net.
For our purposes, Socks2HTTP allows us to integrate MIRC with Multiproxy. To configure the applications, perform the following steps:
In Socks2HTTP:
check the option "Try to detect proxy automatically."
In the field that says SOCKS port, enter 8088 (or whatever port you are using with multiproxy).
In MIRC
Open Options>Connect>Firewall
Check the Use Firewall box
For Protocol, check Socks 5
For hostname, enter 127.0.0.1
For Port, enter 8088
This is shown in Fig. 6.
You can now use IRC with total anonymity.
TIP
Using this configuration, you never have to worry about being banned from an IRC server again (or any server, for that matter). Simply spin multiproxy to a new anonymous proxy, change your alias, and you will be able to circumvent the ban.
Counterintelligence
Once you have successfully masked your identity online, you can proceed to gather data. This is when a bit of social engineering skill comes in handy. If you show genuine interest and enthusiasm, many hackers will soon trust you enough to give up their precious custom exploits, which may be known to only a handful of people in the entire world.
A more advanced technique is to perform your own defacements on authorized sites, i.e., perform cleverly faked attacks on networks that you secretly have (written) permission to legally penetrate. The FBI recently used this tactic to successfully infiltrate a number of hacker groups over a six-month period.
Summary
By using the techniques in this article with skill and perseverance, you will soon find that you have access to exploits far in advance of public knowledge. Using systemized infiltration, within a short period you can develop a sophisticated, global network of security intelligence.
In closing, there are a few words of caution to keep in mind. Remember that these techniques are dangerous and should be supervised by trained law enforcement organizations. In addition, if you do happen to come across camped exploits, make sure to promptly report them to the proper authorities. Finally, it is tempting to dismiss young hackers as "script kiddies", but keep in mind that these hackers are just like the ones that reportedly have penetrated the United States Central Intelligence Agency (CIA) and other highly secure networks. For example, one hacking group with an estimated average member age of 16 defaced nearly one hundred security consulting websites in the same day. In fact, according to attrition.org, one website with its own Bugtraq was itself defaced: Security Focus had its banner advertisements indirectly replaced for several hours by a group of young hackers known as Fluffi Bunni. This group, whose mascot is a stuffed pink rabbit, jokingly altered the site banner advertisements from "Security Focus" to "Security Fluffi" (fig. 7). Fortunately, by applying the simple counter-intelligence techniques outlined in this chapter, such embarrassing compromises can often be easily prevented.





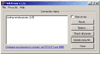 Fig.
1
Fig.
1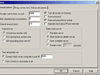 Fig.
2
Fig.
2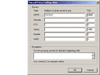 Fig.
3
Fig.
3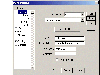 Fig.
4
Fig.
4 Fig.
5
Fig.
5 Fig.
6
Fig.
6 Fig.
7
Fig.
7 Digg
Digg
 Del.icio.us
Del.icio.us
 Your Account
Your Account






 Account Sign In
Account Sign In View your cart
View your cart