Operations Security: Hips don’t lie, and neither do loose lips
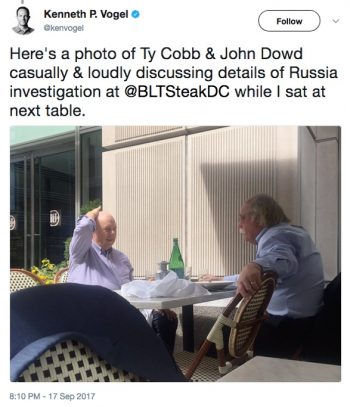
So, I was chatting with my Twitter buddy @GlobalMarshal the other day (side note: he asked to be referred to as my soulmate, so I’m just leaving that here) and he pointed me to a recent story that was equal parts hilarious, sad, and scary. A NY Times journalist having lunch at a DC restaurant overheard White House lawyers loudly and publicly discussing the Russia investigation. Now I get working lunches, but this seems a bit…excessive.
Moving on, there was a recent story in which a bored Russian soldier’s geo-located posts to Instagram indicated that he was actually hanging about in the Ukraine instead of where he should have been, safely nestled inside of Mother Russia’s borders.
And finally, my favorite, the famous Facebook engagement picture in which the couple failed to Photoshop out the used pregnancy test in the corner!

What do all of these faux pas have in common? My friends, let me acquaint you with the concept of Operations Security. According to NIST 800-53, Operations Security is “…a systematic process by which potential adversaries can be denied information about the capabilities and intentions of organizations by identifying, controlling, and protecting generally unclassified information that specifically relates to the planning and execution of sensitive organizational activities.” In English, it simply means that OPSEC is about shutting the heck up about stuff, even if it doesn’t seem important. It was originally a military concept, but in this day, applies to governments, organizations, and YOU!
OPSEC in The Business World
As a security professional, I imagine you are bombarded daily with stories about obvious bad infosecurity…the passwords written on sticky notes, the tailgating, BAD PATCH MANAGEMENT, the list goes on. But what about the sneaky stuff that’s sneaky because it just doesn’t seem like a big deal?
An observant and motivated attacker will make it their mission to collect everything about you and your company. If you’re not careful about what you disclose, these pieces of information can paint a pretty clear picture about what you and your organization are up to. This in turn can be used in a multitude of malicious ways. At SEORG we speak most often about the use of information in the creation of personalized messaging such as spear phishing. But consider for a moment what kind of harm could occur at an organizational level if someone could determine how, and with whom, you do business, future plans, personnel changes and corporate strategies? What if this attacker worked for a competing company or adversarial nation state?
In the course of our social engineering work, we have, no kidding, collected information that included:
- The fact that key staff members would be absent from an organization, travel plans to include detailed itineraries and passport information – both from personal social media and vishing of helpful admins
- Information on proprietary and future product lines – both from personal social media and vishing calls
- Financial information on a number of companies – from online OSINT and vishing
- Potential corporate expansion plans – directly and indirectly from online OSINT and vishing calls
- Proprietary information on corporate vendors and partnerships – directly from online research, personal social media, and other public sources such as online forums
When I was in the military, we weren’t even allowed to tell people where we WEREN’T being deployed to ensure someone couldn’t inadvertently guess. Can you imagine how that would have gone?
Dear mom,
I’m leaving the country for more than 30 days but less than 90 days. I won’t be in Europe, Asia, Africa, the Mediterranean, either of thepoles, or the Middle East. Please feed Fluffy and water my plants. Love you, bai.
Yeah, that didn’t play, and that’s the essence of OPSEC. As best as possible, don’t leave any breadcrumbs for an adversary to follow. Even non-information can help someone figure out what you’re up to.
NIST 800-53
According to NIST, OPSEC involves i) identifying critical information, ii) analyzing threats, iii) analyzing vulnerabilities, iv) assessing risks, and v) applying countermeasures. Simple concepts, but not easy by a long shot. Who knew that posting a happy engagement picture would lead to the world knowing about your future parental status?
Good OPSEC is a huge job and takes constant work. There’s always a tendency to get into our normal routines and think nothing of posting pictures, complaining online about bad vendors, and sharing good news about promotions and vacations. There’s also the rather typical mindset of “Why would anyone target me?” Regardless of whether or not it’s true, you have to believe and act as if someone IS watching you and IS putting together a dossier that includes everything down to your dog’s name.
So Where Do I Start?
First, figure out what it is you need to protect. It might be anything from personally identifying information all the way up to trademarked corporate property. Although this might seem obvious, knowing what you need to protect will help you determine the ways that an uninvited guest could get to it.
Second, figure out the information that’s available for anyone to find.
If you’re a civilian, learn that Google is your friend. You need to know the information that’s out there and available on you. Learn how to do Google searches on yourself; there are plenty of guides out there.
I’m not just talking about your drunk bachelor party photos on Facebook. Entities with access to your information can post it freely without your consent. Did you buy a house or contract work on your home that required a permit? Do you retain licensure in a profession? Do you have children who are enrolled in school? Does your mom Instagram every family occasion with geo-location turned on? Does one of your LinkedIn connections allow viewing of all of his/her connections? Is your Amazon wish list public? You’ll likely find all of this information in a few simple searches.
If you’re an infosec pro, your job is even bigger. You’re not only responsible for yourself, but your organization. Now you’re talking about getting PR, legal, customer service, and HR on board. The jobs of these groups are often to communicate openly to the public, business partners, clients, and investors and that is at direct odds with good OPSEC. You will also need to decide if and how to manage corporate policy with respect to the social media habits of all of your employees.
Anyone of a certain age will remember the scene in Trading Places when Winthorpe, after seeing large paychecks written to a certain Clarence Beekes and a news report that he was transporting the orange juice crop report, exclaims, “My God! The Dukes are going to corner the entire frozen orange juice market!” What a fun and obviously Hollwood-esque example of bad OPSEC, right?

What if I told you that a social engineer found an article about the opening of a new corporate facility, watched sites such as LinkedIn and Glassdoor for new hires, made a few vishing calls to determine that certain materials are being purchased…and with that concluded that a company was planning to develop a ground-breaking new product! Sound impossible? We’ve done that in the course of our social engineering engagements. The key here is that no one piece of information we obtained was considered classified. But when pieced together, it created a picture that any competitor would have been happy to have.
Third; lock down what you can. This is the hard one. You can’t lock everything down unless you are willing to live completely off the grid and cut off ties with friends and family. You should, however, be aware of privacy options online and how entities can use your information. Understand your risk and minimize your exposure when you can.
Finally; train your staff and have consistent and clear incident response in place. Unfortunately, it’s no longer a case of IF something happens. But understanding the concept of OPSEC is a solid way of hardening your defenses by learning to actively deny your adversaries information.
Please note that this isn’t everything you need to know about OPSEC, but I hope this article helped bring a little attention to the subject. Thanks for reading, and as always, stay safe!
Written By: Michele Fincher
Sources:
https://twitter.com/GlobalMarshal
https://www.nytimes.com/2017/09/19/us/politics/isnt-that-the-trump-lawyer-a-reporters-accidental-scoop.html?_r=0
https://arstechnica.com/tech-policy/2014/08/opposite-of-opsec-russian-soldier-posts-selfies-from-inside-ukraine/
https://www.dailymail.co.uk/femail/article-3265298/Woman-shares-engagement-picture-Facebook-accidentally-includes-PREGNANCY-TEST-image.html
https://nvd.nist.gov/800-53/Rev4/control/SC-38
https://support.google.com/websearch/answer/2466433

