Recent headlines have thrown social engineering tactics back into the spotlight and with the election, it’s no wonder that the candidates are the primary targets of attacks. In recent months Robert Podesta, Colin Powell and the Democratic National Convention have had emails dumped to WikiLeaks by persons unknown. While many of these are attributed to a certain group, the goal here is not to look at the attribution but the method.
When looking at a suspicious email from any service, you should always check the sender and ask yourself, “Did I expect this message or do I know this person?” If the answer to that is no, then you should absolutely look closer. If the service is one you use, go directly to the service itself. Don’t use links provided in an email, because concealing malicious links is very easy. In fact, according to a study by RSA, URL shorteners like Bitly and tiny.url have been heavily used in recent months. In the case of Podesta, the Bitly address was embedded into the google.com URL as a redirect. The following graphic was pulled from an Ars Technica article, and we have added some flags to look for that may indicate a phish.
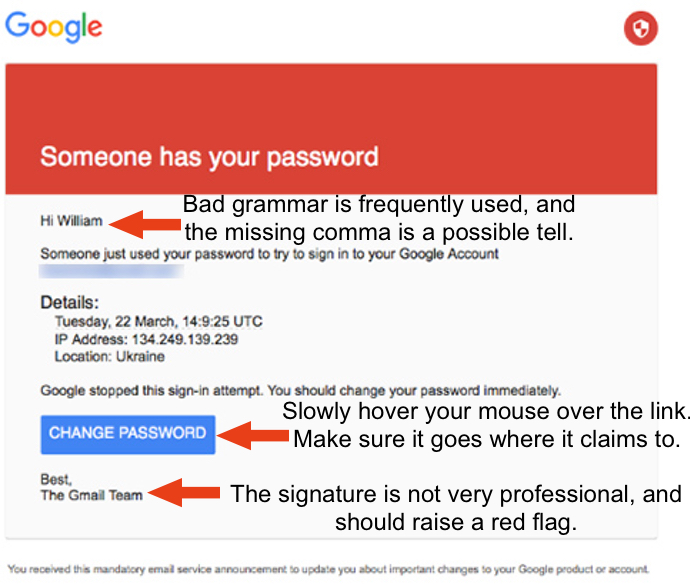
Figure 1: A few flags to look for in emails to help spot a fake.
Another thing that went wrong here was that though the IT staff were fooled by the spear, they issued advice (namely, to go to gmail.com directly and change the password and enact 2FA) which was best practice; however, the staffers or Podesta himself simply clicked the link. If you go to an IT professional and ask their advice, it’s probably a best practice to follow that advice. Once again, don’t click links in emails; rather, navigate to the known good website directly and see if the information is true or to make any requested changes to your account.
In conclusion, any time you receive an email:
- Look carefully at the sender address
- Don’t click any links, rather navigate to the site directly
- If it’s at all possible, enable 2 Factor Authentication
Following some basic guidelines can dramatically reduce your attack surface and help keep you and your organization safe online.
Sources:
https://community.rsa.com/servlet/JiveServlet/downloadBody/58632-102-1-57322/2016_Q2_FraudAction_Quarterly_ThreatReport.pdf
http://arstechnica.com/security/2016/10/russia-linked-phishing-campaign-behind-the-dnc-breach-also-hit-podesta-powell/
http://motherboard.vice.com/read/how-hackers-broke-into-john-podesta-and-colin-powells-gmail-accounts
2 Comments
Comments are closed.


nice article…
An informative blog post, that isn’t full of non-qualified information! At last! It is rare these days. I have been in the industry for a while now and I like to read up on whats new daily. Usually I read in article and I am so disappointed afterwards because I feel the article has been based on estimates. This however I have full trust in, so thank you.