Phishing
At Social-Engineer, we define phishing as the “practice of sending emails appearing to be from reputable sources with the goal of influencing or gaining personal information.” (Hadnagy, Fincher. Phishing Dark Waters: The Offensive and Defensive Sides of Malicious Emails. Wiley, 2015). Phishing is one of the biggest cybercrime threats facing organizations and individuals today. According to the 2021 Verizon’s Data Breach Investigations Report (DBIR) since 2017, social engineering attacks as a pattern continue to increase, with Business Email Compromise (BEC) breaches doubling again since 2020.
Bad actors often impersonate well-known institutions, such as the IRS, banks, or businesses. In addition, attackers may impersonate individuals such as your boss, a co-worker, or perhaps your real estate agent. The goal of the phishing email is to lure you into opening an attachment that has malware or clicking a link to a spoofed website. Of course, there are many different types of phishing attacks and we will highlight several. In this article we’ll discuss URL and email manipulation, common phishing vectors, spear phishing, and whaling. We’ll also discuss how adversarial simulators use phishing in security audits.
NOTICE: Never use this information to perform illegal acts! The purpose of the Social Engineering Framework is to help ethical social engineers learn the skills they need in their adversarial simulation jobs. We also discuss these details to educate organizations about possible social engineering attacks. This will also help organizations decide which services may help them defend against these attacks.
URL and Email Manipulation
People trust messages from well-known, reputable sources. For this reason, a common phishing tactic bad actors use is to manipulate a URL, also known as typo-squatting. Criminals know that if the URL looks close enough to a trusted site, the odds are they can fool you to click on it. For example, when a user scans over a URL like http://www.company.com, it looks almost identical to http://www.cornpany.com if the font is right. Did you notice the difference? The malicious URL is coRNpany.com instead of coMpany.com. Another example is support.amazon.com versus the more dangerous support-amazon.com. Again, did you notice the difference? The malicious URL is support(dash)amazon instead of support(dot)amazon. Surprisingly, URL manipulation requires very little time or effort. The bad actor buys a domain that closely resembles the legitimate URL. After that they will set up an email account and spoof the website.
Common Phishing Vectors
We outline four common phishing vectors, which we will explore in more depth. They are:
-
- Current Events
- Charities
- Financial
- Government
Current Events
Bad actors take advantage of current events such as disasters, large public events, holidays, or data breaches to phish large groups of targets for information. For instance, cybercriminals quickly exploited the COVID-19 pandemic. According to a report from The Federal Trade Commission (FTC), there were 71, 026 COVID-19 and stimulus fraud cases reported, with a total of $89.51M in total loses.
Another example is the 2017 Equifax data breach. Shortly after the data breach, The Better Business Bureau (BBB) issued an alert that scammers had created 194 phishing websites just one day after the breach and launch of legitimate help websites. The BBB also warned about phishing emails requesting verification of transactions or to check account status.
Charity Scams
The devastating Camp and Woosley fires in California in November 2018 left countless families homeless and grief-stricken. Attackers were quick to take advantage of this distressing tragedy. Agari issued an alert warning that criminals were specifically targeting workplaces. Posing as the targeted enterprise’s CEO (Chief Executive Officer), the attackers sent emails to employees in accounting, finance, or administration with instructions to buy gift cards to supply financial help for clients who were fire victims. For more information on charity scams, please check out our newsletter here.
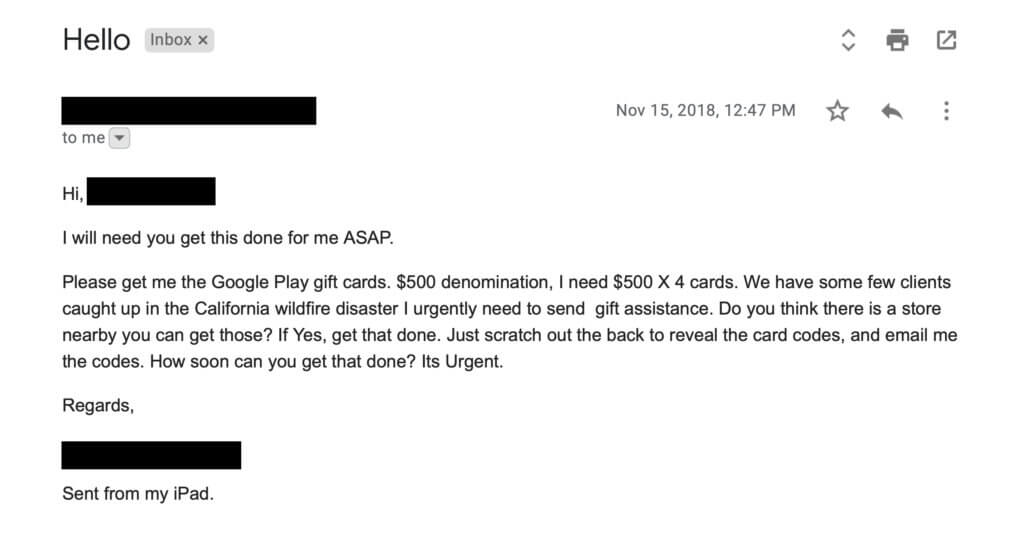
Image: Agari
You might also see charity phishing scams on Twitter or text/SMS as well. For more information, please see the Framework SMiShing page.
Financial
Posing as a financial institution is another common tactic of bad actors. Criminals know that if they send out mass emails posing as a well-known bank, the probability that it happens to be your bank is high. In some cases, they may even know that it’s your bank. If that’s the case, they may include your name and address in the email. Their goal? To have you click a link or open an attachment.
A recent phishing campaign was reported to be impersonating Citibank. The email included a link to a legitimate-looking website with ‘update-citi.com’ as the domain address. Users who received the email were requested to enter their online banking credentials as well as personal information.
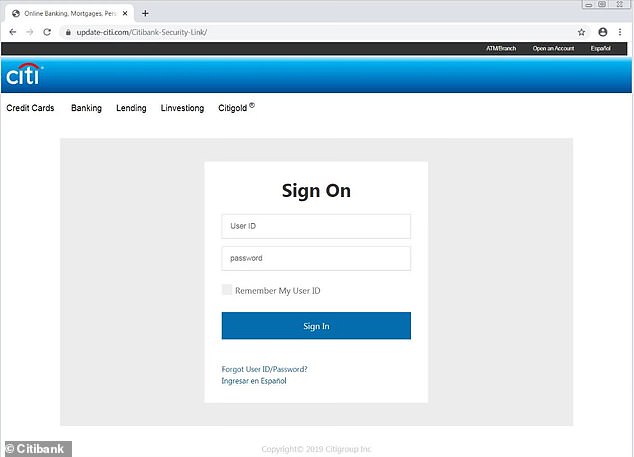
Image: DailyMail.com
Government
Government agencies, such as the Internal Revenue Service (IRS), are commonly impersonated by criminals. In fact, over the past several years, phishing has made the IRS Dirty Dozen list for tax scams. Notably, during the coronavirus pandemic, many phishing tax phishing scams were circulating using keywords such as, “coronavirus,” “COVID-19,” and “stimulus.”
Another IRS phishing email circulating is the Tax Account Transcript scam. In this scam, criminals send emails pretending to be from “IRS Online” with an attachment labeled “Tax Account Transcript” as bait to entice users to open documents having malware. When the attachment is opened, malware is unleashed. In other tax scams, attackers send phishing emails with the instruction to “update your IRS e-file immediately.” When the intended victim clicks the link, they are taken to a fake website that spoofs the official IRS website.
Ransomware
Cybercriminals are also attacking critical infrastructure, municipal governments, businesses, and the healthcare sector through ransomware—often spread through phishing emails that have malicious code.
In spring of 2021, a ransomware attack on Colonial Pipeline, the largest in the U.S, crippled production, producing concerns of widespread fuel shortages. Ransomware attacks, such as recently reported in Gary, Indiana, have also crippled municipal governments, leaving them scrambling to restore services. Ransomware attacks reached unprecedented levels during the COVID-19 pandemic that started in 2020. In fact, the Healthcare sector alone saw a 580% jump in ransomware attacks. These attacks left many organizations wondering how to mitigate the risks that ransomware attacks pose.
Spear Phishing
Due to the success of phishing attacks, cybercriminals have developed a refined technique known as spear phishing. A spear phishing email is more targeted than a general phishing email. Instead of sending out thousands of emails hoping to catch a few random victims, spear phishing targets specific higher-profile people who have access to something the attacker wants. Cybercriminals conduct open-source intelligence (OSINT) to craft an email that specifically caters to the recipient’s job, personal situation, or preferences. Additionally, they use data from previous breaches to assist in current attacks.
The pervasive use of social media supplies a gold mine of personal data that attackers can use. Because of our culture of sharing, individuals are equipping attackers with all the information they need without realizing it. The smallest bit of information, such as profile pictures, can put the attacker on track to creating a solid phish.
One spear phishing campaign found making the rounds specifically targets Human Resource (HR) employees. As reported by VadeSecure, an HR director in the construction industry was targeted. Posing as the Chief Operating Officer (COO), the criminal emailed the HR director. The request? The “COO” wanted to make changes to his Payroll Direct Deposit Account. By posing as the COO, the attacker is hoping for two things; 1.) the HR director will feel pressure to respond quickly and 2.) there will be a higher payout.
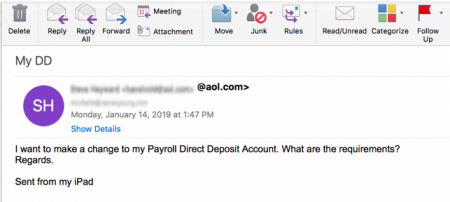
Image: VadeSecure
Whaling
Whaling is a highly targeted attack designed to strike at an organization’s “big phish.” A big phish is a high-value individual such as a senior executive, a high-level official in private business, or anyone with privileged access to government (or top secret) information. These high-value targets have credentials or access that, if compromised, could endanger the entire business. Like spear phishing, these attacks can be more difficult to detect because of their stealth and because they are generally sent on a one-time basis.
The City Treasurer of Ottawa, Marian Simulik became a victim of a whaling attack. She received the following email, purportedly from her boss, city manager Steve Kanellakos, and approved the transfer of $97,797.20 in funds. The email reads in part:
“Okay, I want you to take care of this for me personally, I have just been informed that we have had an offer accepted by a new international vendor, to complete an acquisition that i have been negotiating privately for some time now, in line with the terms agreed, we will need to make a down payment of 30% of their total, which will be $97,797.20. Until we are in a position to formally announce the acquisition, I do not want you discussing it with anybody in the office, any question please email me. Can you confirm if international wire transfer can go out this morning?”
Why Adversarial Simulators Use Phishing in Security Audits
Professional Adversarial Simulators primarily use phishing for the following purposes:
- As part of an adversarial simulation, usually leading to a controlled compromise of the organization’s digital or human network. The exposed vulnerabilities are reported in detail to allow the organization to strengthen their security.
- As part of a security awareness program throughout the year, with the focus on educating users on the different levels of phishing.
- To set a baseline for assessing user susceptibility to phishing attacks and to justify future training on the topic.
Companies spend thousands of dollars on IDS (Intrusion Detection System) appliances, firewalls and other protection devices to watch the network. However, just one skilled phishing attack can lead to total devastation in a company. While technical solutions exist to stop phishing attacks, there is no practical way to prevent an employee from clicking links, opening attachments, or filling out forms. The best defense is to educate employees and ensure they understand the threats posed by phishing attacks. As a result, they are less likely to click malicious links, and more likely to report suspicious activity. To this end, security awareness training such as Managed Phishing Service equips leadership to know how their organization will respond to phishing attacks.
Reference:
Phishing Dark Waters: The Offensive and Defensive Sides of Malicious E-mails. Indianapolis: John Wiley & Sons, 2015. Print.

