
It’s hard to believe that Social-Engineer.org (SEORG) has been hosting the SECTF event for the past eight years. From small beginnings in 2010 the SECTF has grown into one of the most anticipated events at the SEVillage.
The amount of interest in the SEVillage and the SECTF competition continues to inspire and humble us. For those of you who have never attended our SECTF event, here’s a little background on it. Contestants gather pieces of information on target companies called ‘flags’. There is an OSINT (open-source intelligence) gathering phase prior to DEF CON and a much-anticipated live call phase during DEF CON.
We use this event to raise awareness of the ongoing threat posed by social engineering and to provide a live demonstration of the techniques and tactics used by potential malicious attackers. Recently, during the 2017 SECTF Webinar, our listeners asked if we could provide information about the competition’s different target companies as well as some basic stats from over the years. We’ve listened and have compiled a review of the eight years we’ve hosted the SECTF competitions. Each year had its own unique feature, observation and fun fact. Let’s begin our journey through SE time, SECTF 8 years in review (2010-2017).
2010 DEF CON 18
The year that started it all! The DEF CON SECTF “How Strong is Your Schmooze” is one of the most ground-breaking events at DEF CON. Target companies in alphabetical order: Apple, BP, Cisco Systems, Coca-Cola, Ford, Google, Mcafee, Microsoft, Pepsi, Phillip Morris, Proctor and Gamble, Shell, Symantec and Walmart. Sorry, folks we do not have the company ranking, best to worst performing for this year.
Companies called: 15
Possible flags: 25
Number of companies with flags captured: 14
Length of contest: 2 days
Total phone calls made: 135
Companies who put up resistance: 7
Employees who put up resistance: 11
Most obtained flag: Popular Tech Info – Open a fake URL
Observation
In some instances, companies managed to evade giving out information on the pretext ‘survey’ call, simply by being “too busy” to deal with it.
Fun Fact
One contestant demonstrated a novel approach; capturing multiple flags without asking any questions. By using assumptive statements that employees felt compelled to correct. The contestant was able to obtain a sizable score without alerting employees that anything was being requested of them.
2011 DEF CON 19
We knew this year would be special and it didn’t disappoint. In addition to SECTF we were excited to introduce for the first time, a separate event, the SECTF4Kids at DEF CON 19. Target companies were selected from retail, airlines, food service, technology and mobile service. They are listed from best to worst performing: AT&T, Symantec, Walmart, McDonalds, Dell, Sysco Foods, IBM, United Airlines, Target, Apple, Conagra Foods, Delta Airlines, Verizon, Oracle.
Companies called: 14
Possible flags: 62
Number of companies with flags captured: 14
Length of contents: 2 days
Companies who put up resistance: 4
Employees who put up resistance: 3
Most obtained flag: Popular Tech Info – Open a fake URL
Observation
Employees at one target company posted very clear pictures of their employee badges on the Internet, which revealed badge design, names and titles. Additionally, a large sample of this company’s employees had extremely detailed personal information readily available such as, names, phone numbers, relatives, addresses, etc. A Google search for “[company] confidential” revealed 61 pages of documents marked confidential, some of which were tagged “[company] Confidential – Highly Restricted.”
Fun Fact
The most difficult pretext, but also the most effective, is the ‘fellow employee’. A fellow employee is often allowed right into the “inner circle” and is given certain information sometimes even without asking. In each case that this pretext was used, large amounts of data were obtained.
2012 DEF CON 20
For 2012 we decided to take the SECTF to a new level. The competition was comprised of two teams; male and female and we called it “The Battle of the SEexes”. Target companies were selected from freight, telecom, oil, retail and tech industries. They are listed from best to worst performing: Shell, Mobil, AT&T, HP, Verizon, FedEx, UPS, Cisco, Target and Walmart.
Target companies: 10
Contestants: 20
Completed calls: 18
Possible flags: 37
Total points by females: 1675
Total points by males: 2329.5
Industries represented: 5
Most obtained flag: Logistics – Do you have a cafeteria?
The guys did a great job! No worries ladies, you totally rocked the following year.
Observation
One large retailer targeted by our contestants had full pictures of employee badges published online for all to see. Using a simple badge-cloning machine, available for about $1000 on the Internet, a criminal could use the published photo to clone a badge and gain access to the facilities. During one of our 5 day training courses held in 2012, we had a student from a major computer company in attendance. All that was needed to clone a badge from his company was 15 minutes and a Google search. The employee was shocked! He stated that our cloned badge would allow us access to their facilities.
Fun Fact
Chris Hadnagy, CEO of Social-Engineer, LLC, packed up the SECTF competition and put it on hold for 20 minutes to meet the director of the NSA, General Keith B. Alexander. It gets even better, General Alexander made a surprise visit to the SECTF while our youngest contestant ever, our very own Hannah Silvers, was in the booth!!

2013 DEF CON 21
For the second year in a row, the SECTF competition pitted men against women. And, this year marked the first year in DEF CON SECTF history that we had more than double the women sign up than we needed and more than 8x the number of men. Target companies were selected from Fortune 500 companies in a diversity of industries and brands commonly used by US consumers. They are listed from best to worst performing: General Electric, General Dynamics, Exxon, Walt Disney, Boeing, Chevron, Johnson & Johnson, Home Depot, General Motors, Apple.
Target companies: 10
Contestants: 20
Completed calls: 51
Possible flags: 37
Total points scored by men: 2,991
Total points scored by women: 3,579
Most obtained flag: Company Wide Tech – What operating system is in use? Closely followed by What browser do they use?
Great job ladies!
Observation
During our 5th consecutive year hosting the SECTF and despite numerous high-profile security breaches, we have not seen consistent improvements that directly address the human factor.
Fun Fact
The winner for 2013 was not a professional social engineer and yet surpassed the next competitor by over 200 total points. She conducted an exceptional amount of research on her target, developed an excellent pretext and was prepared. She attributed her background in theater and improv as a key element that helped her stay flexible and adapt to whatever was thrown at her.
2014 DEF CON 22
For our 5th anniversary hosting SECTF we decided to change things up. Contestants were grouped into teams of two and required to interchangeably engage with targets during the live call portion without raising suspicion. We selected target companies from retail that specifically deal with point-of-sale. Listed from best to worst performing: Lowe’s, Macy’s, Walgreens, Staples, Costco, Rite Aid, Wal-Mart, CVS, The Home Depot.
Target companies: 9
Contestants: 18
Completed calls: 121
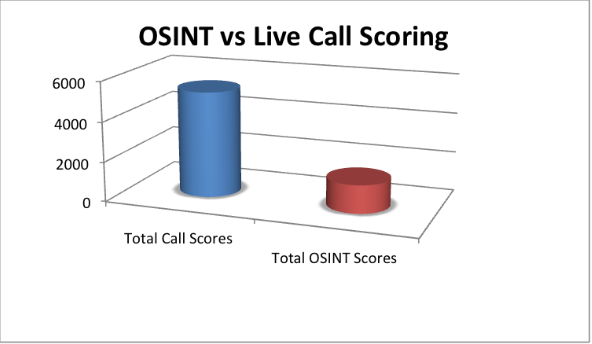
Total points scored on reports: 1407
Total points scored on calls: 5306
Most obtained flag: Other Tech – Is wireless in use on site? (yes/no).
Observation
2014 saw a complete reversal in total points awarded for OSINT versus total points awarded for live calls. Watch the webinar to find out what conclusions we extrapolated from this reversal.
Fun Fact
For the first time contestants submitted a video explaining why they should be part of the SECTF.
2015 DEF CON 23
2015 proved to be The Year of Data. We hired a developer who created an automated scoring system for us so that we could capture everything, and we did. This enabled us to provide a truly amazing report of the OSINT and live call phase of the SECTF competition. We selected targets from telecommunications providers. They are listed from best to worst performing: Frontier Communications, Vonage, Sprint Corporation, DirecTV, Windstream Communications, AT&T, Dish Network, U.S. Cellular, Century Link, Virgin Media, Verizon Wireless, T-Mobile. Two companies were not called; Comcast and Time Warner Cable.
Competitors: 14
Completed calls: 150
Total points scored on reports: 1696
Total points scored on calls: 6772
Most obtained flag: Company Wide Tech – What operating system is in use?
Observation
There appeared to be very little relation between the success of the call and the use of caller ID spoofing. Although professional social engineers rely consistently on caller ID spoofing, our finding may be an indicator that the ability to spoof has a greater effect on the caller’s confidence and comfort level than on the target’s compliance. In addition, many employees, particularly executive level individuals, had LinkedIn accounts that were not private, providing significant information to attackers.
Fun Fact
A coin toss at the beginning of each contestant’s time slot determined the ability to spoof.
2016 DEF CON 24
2016 was another great year for us at DEF CON. After many hours watching submission videos, our panel made selections based on several factors, such as, the contestant’s desire to learn as well as our perception of the contestant’s intent. As this is an educational event, we wish our participants to have a very strong emphasis on ultimately helping the status of corporate security as opposed to the singular goal of “winning” an engagement. We selected the target companies from the security industry. Listed from best to worst performing: Symantec Corporation, IBM, Oracle Corporation, EMC Corporation, SYNNEX Corporation, Palo Alto Networks, Fortinet, Dell Secure Works, Sophos Group, Akamai Technologies, Cisco Systems, RSA Security, Deloitte and Comcast Xfinity.
Target companies: 14
Competitors: 14
Completed calls: 160
Total points scored on reports: 1698
Total points scored on calls: 4352
Most obtained flag: Employee Specific Info – How long have they worked for the company?
Observation
Social media continues to be a potential hazard for organizations and their employees. Pictures posted online often reveal sensitive information (e.g., badges, hardware in use, other details about physical space).
Fun Facts
Chris Hadnagy and Michele Fincher provided a live demonstration of the techniques and tactics of vishing.
This was the first year that every single one of our competitors showed up on time and ready to go. No panic-filled replacements required.
Watch as Michele owns the identity of CBC News’ Asha Tomilson.
2017 DEF CON 25 and DerbyCon
This was an exciting and unique year for us. For the very first time, SEORG hosted two SECTF contests; the SECTF at DEF CON and the SECTF at DerbyCon. Additionally, it was our very first SECTF4Teens competition held at the SEVillage at DEF CON. We selected the target companies for DEF CON from the gaming industry. From best to worst performing: Warner Brothers Games, Rockstar Games, 2K Games, Electronic Arts, Disney, Activision Blizzard, Bandai Namco Entertainment, Nintendo, Hasbro, Ubisoft Entertainment, Sega Games, Bethesda Game Studios, Sony, Mattel.
Target companies: 14
Competitors: 14
Attempted calls (logged): 114
Total points scored on reports: 1774
Total points scored on calls: 2360
Most obtained flag: Employee Specific Info – How long have they worked for the company?
We selected the target companies for DerbyCon from Fortune 500 companies started in Louisville, KY. From best to worst performing: Papa-John’s International, Tempur-Pedic, Yum! Brands, Brown-Forman Corporation, Ashland and GE Appliances.
Target companies: 6
Competitors: 6
Attempted calls (logged): 80
Total points scored on reports: 725
Total points scored on calls: 1642
Most Obtained Flag: Other Tech – Do you block websites?
Observation
During the OSINT phase, the contestants successfully gathered data on target companies using simple online searches. This reveals how challenging it is for organizations to control the social media postings of current and/or past employees. It’s important to realize, if competitors found valuable information through these sources, then certainly malicious attackers can as well.
Fun Facts
Chris Kirsch, 2017 SECTF winner at DEF CON and Chris Hadnagy re-enacted the winning phone call.
We organize flags in the order that we want. However, contestants that tend to do better during the live call phase, reorganize their flags to make their call more realistic.
Conclusion
We hope you enjoyed this journey through SE time. If you would like to do more reading on the different competitions, The SECTF reports and webinars are available to download in the resources section of our website. Please check back with us for posted updates for the SECTF DEF CON 26 rules and regulations. See you in Vegas.
Sources:
https://www.social-engineer.org/resources/sevillage-def-con-25/
https://www.social-engineer.org/resources/watch-live-recording-sectf-results/
https://www.social-engineer.org/general-blog/sectf4kids/
https://www.social-engineer.org/general-blog/defcon-20-what-the-heck-just-happened/
https://www.social-engineer.org/social-engineering/a-lesson-from-a-young-social-engineer/
https://www.social-engineer.org/social-engineering/winning-sectf/
https://www.social-engineer.org/resources/sectf-webinar-def-con-22/
https://www.social-engineer.org/sevillage-def-con/the-sectf4teens/
http://www.social-engineer.com/about/
https://www.veracode.com/blog/security-news/how-single-phone-call-can-compromise-your-company
https://www.social-engineer.org/resources/

