Malicious attackers are tireless as they search for personal and professional information; and they want it all. Indeed, information provides attackers with the knowledge they need to coordinate an approach eliciting a specific emotional response. Their goal? To achieve a compromise or breach. Where are they finding all of this personal and professional information? Let’s take a look at one method used; social media platforms, such as Facebook and LinkedIn. Doing so will help us in two areas: 1) it will inform us as to why we need to vigilantly protect personal and professional information, and 2) it will identify areas of vulnerability to strengthen through education and training. It’s important to realize that we can get burned by overexposure on social media.
Have you noticed how much people share about their lives on Facebook? Think of all the personal information that you post. For instance, do you post your family connections, birthdays, anniversaries, work, hobbies, vacations, pets, the summer camp the kids went to, favorite restaurants, charities, as well as social and political interests. And, of course, you probably post photos, photos, and more photos.
LinkedIn has become one of the most popular social platforms for professionals. If you have an account, think about what you include in your profile; name, photo, location, occupation, work experience/history, education, special interests, and groups you follow.
Social media platforms have made it easier than ever before for attackers to collect information. Moreover, LinkedIn presents a real Catch-22. Indeed, organizations as well as their employees want to have an up-to-date and active presence. However, bad actors can exploit that presence in social engineering and phishing attacks. In view of this, let’s see how attackers made use of social media platforms to gather information resulting in a compromise and breach.
Mia Ash
In case you haven’t heard about ‘Mia Ash’, her Facebook profile and picture describe her as an attractive British woman with two art degrees and a successful photography business called, “Mia’s Photography”. In reality though, she is a persona created by Iranian state sponsored spies known as OilRig/COBALT GYPSY. Although the persona is fake, the pictures are very real. Attackers literally stole hundreds of photos from several social media accounts belonging to a Romanian photographer and student.
The Role of Social Media in Information Gathering
While using an attractive woman as a honeytrap is nothing new, our focus is on the role of social media platforms to gather information for the attack. If an initial generic phishing attempt did not result in the hoped for click, Mia Ash would use LinkedIn to search out employees from the targeted organizations with job titles that suggested administrative or elevated access to the targeted corporate network.
When Mia Ash found an employee with the right credentials, she would connect with him on LinkedIn. The typical conversation was about his job, her photography business, and various trips she took. After establishing a rapport on LinkedIn she would then invite the employee to continue the conversation on Facebook. After spending months cultivating a relationship with the employee, Mia would ostensibly ask for assistance in connection with her photography business; setting the stage for the attack. The compromise of the individual was not the ultimate goal, but rather served as the launching pad.
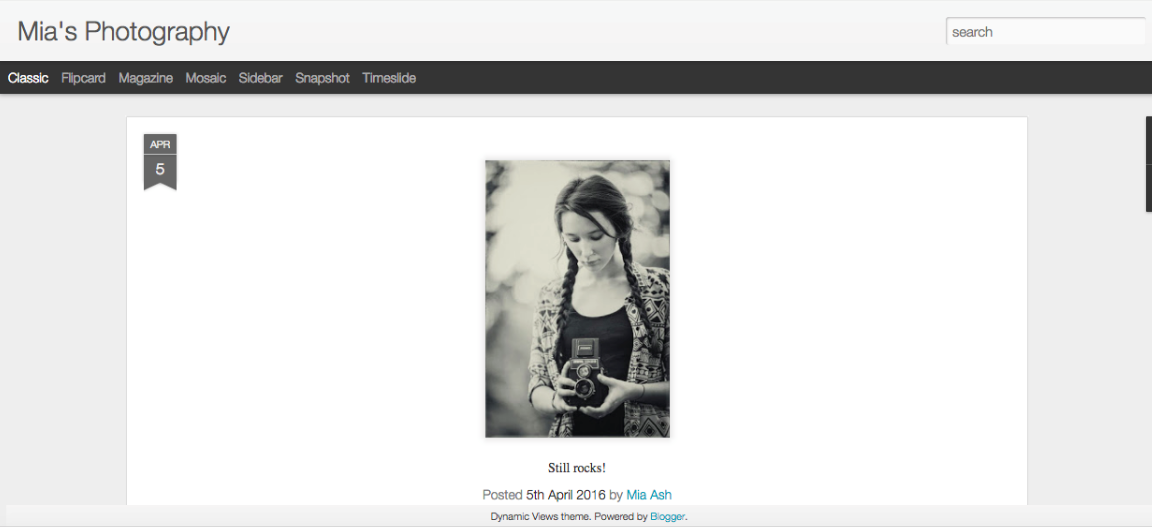
Mia Ash and Deloitte
In July 2016, Mia Ash targeted one of the Big Four accounting firms, Deloitte. To start with, she engaged a cybersecurity employee on LinkedIn in conversations regarding his job. Next, she built rapport and trust through photo sharing and messaging. In fact, the Deloitte employee even offered to help Mia Ash set up a website for her photography business. Finally, the reconnaissance and information gathering paid off. She set the stage to initiate the attack, a phishing email. Mia Ash allegedly convinced the Deloitte employee to open a file containing some of her photos on his work laptop. The email containing the photos was booby-trapped with the malware dubbed, PupyRAT designed to pilfer credentials.
Mia Ash and a Middle Eastern Company
As reported by SecureWorks, Mia Ash used LinkedIn to search out and contact an employee from the targeted organization with questions about you guessed it, photography. Mia Ash and the employee messaged each other about their professions, photography and their travels. Mia then asked if he would add her as a Facebook friend so that they could continue their conversations there. About a month later she asked him to participate in a photography survey. Once again, she set the stage for the attack, a phishing email. A Microsoft Excel document, “Copy of Photography Survey.xlsm”, was sent to his personal email account. Mia told him that the survey would only function properly if opened in his corporate email account. He complied; the attached survey contained macros that he enabled unleashing PupyRAT.
Elianna and the IDF (Israeli Defense Forces)
Hamas operatives created fake Facebook profiles of attractive young women. Their goal? To entice unsuspecting IDF soldiers into installing a virus that would turn their mobile device into an open book. Contacts, location, apps, pictures would become accessible to Hamas operatives; compromising the soldier and potentially the IDF organization. How did Hamas operatives find their targets? It is reasonable to conclude that social media platforms, as well as online search engines, produced the information needed. All targeted IDF soldiers were found through public photos with tags and posts revealing they were active in IDF military service.
Don’t Get Burned By Overexposure
The persistent use of social media platforms to locate potential victims indicates that this method of information gathering is highly successful. Elaborate social engineering attacks were orchestrated with devastating consequences. In the attack against Deloitte, it’s notable that a cybersecurity employee fell victim to the con.
The dangers of overexposure, both personal and professional, on social media platforms is not a new topic for us. We’ve discussed it in our Newsletters, and in the Framework. However, from these recent examples it’s evident that we can’t let out guard down. So, what can we do?
Lock Down Social Media Accounts
When it comes to personal and professional information posted to a social media platform think ‘security first”. TRY THIS: Google your name and see what information and pictures are available. Ask yourself: Would I want anyone to see it? Should this information be protected? If so, don’t get burned by overexposure. Lock the information down with privacy settings, or consider not posting at all. Take the time needed to become a privacy settings ‘expert’. Here’s a place to start: Facebook’s Privacy Basics, including Manage Your Privacy and Staying Safe and Secure. Also, know the privacy settings on LinkedIn and how to implement them. Consider changing the ‘public’ and ‘all members’ setting to ‘connections’ only.
Before accepting social media connection requests, validate the user’s authenticity. Clear guidelines for social media usage, as well as education for identifying potential phishing lures are essential for executives and employees. Clear company policies need to be in place for reporting potential phishing messages received through corporate email, personal email, and social media platforms.
Conclusion
Let’s not be content with just a check box approach to training. Ongoing training that is both customized and interactive can mitigate the threat of a data breach due to overexposure on social media.
“Tell me and I forget. Teach me and I remember. Involve me and I learn.” – allegedly Benjamin Franklin, probably Xun Kuang.
Sources:
https://www.secureworks.com/research/the-curious-case-of-mia-ashhttp://www.claws.in/1800/to-believe-or-not-to-believe-mia-ash-debashish-bose.html
https://www.wired.com/story/iran-hackers-social-engineering-mia-ash/
https://nakedsecurity.sophos.com/2017/01/23/israeli-soldiers-duped-into-installing-malware-via-fake-facebook-profiles/
http://www.ehackingnews.com/2017/10/iranian-hackers-target-deloittes.html
https://www.forbes.com/sites/thomasbrewster/2017/10/05/facebook-fake-hacks-deloitte-employee-iran-cyber-spies-suspected/#9222aed188c7
http://money.cnn.com/2017/07/27/technology/business/cobalt-gypsy-oilrig-linkedin-photographer/index.html
https://www.knowbe4.com/press/knowbe4-releases-q3-2017-top-clicked-phishing-report
3 Comments
Comments are closed.


It is an amazing article. Even though there is a swing towards social media safety, we tend to forget the basic privacy guidelines for using social media. Here are few tips to help protect us from social media attacks:
1) Password: Use different password for different social media accounts, along with long and strong passwords.
2) Selectively accept friend requests and follow requests on social media.
3) Scrutinise what you are sharing on social media. Don’t reveal sensitive and personal information such as home address, contact number etc.
4) Don’t click on random or spam links posted anywhere
5) Keep your softwares and computers updated. Install an antivirus on your device.
6) Always logout the social media accounts