Have you ever been in the middle of a family dinner or event and the patriarchal family members start discussing the “good ol’ days”? Inevitably, you hear the famous line, “When I was your age, we didn’t even lock our doors at night.” For those of us who didn’t grow up in that generation, we shake our heads, thinking that’s an insane thing to do. Today, we have multiple locks on our doors and windows that we check and double-check before we go to bed. On top of that, we have alarm systems that tell us when someone has broken those locks. Additionally, security cameras and smart devices record video and monitor any movement outside and inside of our homes. Even with all of these mechanisms and systems, we often still don’t feel safe. I think it’s safe to say we are far from the “good ol’ days.”
The same is true when it comes to corporate security. Daily, there are reports of new attack vectors that criminals are using. Incidents, breaches, vulnerabilities, bugs, and exploits are suffocating the security ecosystem. As a result, there is more to worry about than ever before. However, unlike our personal security, the corporate front door is often not as secure as the front door of our own homes. But what is the front door of your company? And why is it so important to know if your company’s front door is secure? Our February newsletter addresses these questions.
The Corporate Front Door
If someone were to contact your company today, whether in person, over the phone, or online, who would open the front door, so to speak? Which of your employees interacts directly with your customers or vendors? Is it your receptionist, an administrative assistant, or perhaps your customer service representatives? Known as frontline employees or staff, these employees are your company’s front door, gatekeepers, and the first line of defense.
Criminals are targeting your front door and searching for vulnerabilities 24/7. The attack usually begins by social engineering frontline employees via email, phone, or in person. What can you do to reinforce the strength of your company’s front door? Let’s look at customer service representatives, call-center agents, as well as receptionists and administrative personnel. We’ll examine the current dangers and provide security awareness tips to bolster your defenses.

Receptionists/Administrative Assistants—A Vulnerable Front Door
Most small-to-medium sized businesses (SMBs) employ receptionists and administrative assistants. They maintain the phone lines, handle customer service matters, manage employees’ information, care for business transactions (both invoices and banking responsibilities). The information they hold is extremely valuable. Further risks exist for these employees as they often handle numerous calls, emails, and queries throughout the day, making them a prime target for malicious attackers. While a lot of money and time is often spent training receptionists and administrative assistants, we find that they are overlooked when it comes to security awareness training. When it comes to risks, organizations often think of their endpoints or critical servers, and don’t consider that their front desk is a rich entry point for social engineers.
My Vishing Story
Before moving to a new role at Social-Engineer, LLC, I was the “front door” for many years. Every call to the company went through me before it got to any other employee, especially those in top management. In my time in that position, I received a variety of interesting calls. One such call was from a gentleman, who was very intent on gaining the personal information of one of our employees. He started by saying he was from a delivery company who was trying in earnest to make a delivery. During our first interaction, I kindly told the man that since we were a remote and virtual company, I could not provide a central delivery address for him to send the package too. Disappointed, the man hung up with me.
Disappointed but Not Deterred
The next day, I received another phone call from the same gentleman. This time, he was more insistent that the package was of high importance and absolutely needed to be delivered to our employee. He pressed me for her home address, insisting that since we could not provide an office address that he would have to send it there. However, we had a strict policy that no personal information was permitted to be given over the phone. Again, I kindly told him that I could not fulfill his request. During these interactions he would repeatedly request to speak to her personally, but that also was not our policy, so he was denied this as well.
The Final Pushback
In the third, and last call I received from this gentleman, he again pushed the urgency of this mysterious parcel. I reminded him, yet again, I could not fulfill his request. I also told him that I had spoken with this employee and she denied ordering or expecting such an important delivery. With those options out of his reach, his final request was for me to verify that he had the right email address. He said he wanted to email her a failure of delivery notice. He recited off a wrong email address, to which I replied “Yep, that should get to her!” With shock the man said, “Oh ok, thank you then.” I never heard from him again, so I never found out how many emails he sent to the wrong address.
Phishing and CEO Impersonation—Attacks on the Corporate Front Door
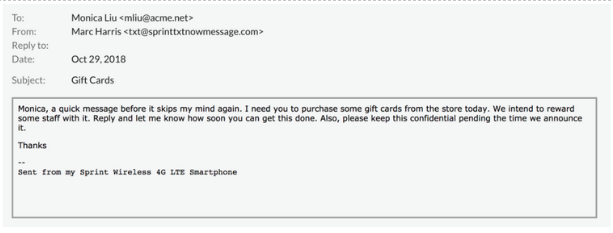
One current attack targeting the front door of organizations is CEO Impersonation. These attacks are successful because they are not only impersonating an authority figure, but they also use timing and context to their advantage. A recent gift card scam was very effective for this reason. The scam directly targeted office managers, executive assistants, and receptionists, knowing that they would be able to fulfill the request of the scammers. These emails appear to be sent from the CEO’s personal account and don’t contain any suspicious links or attachments. But they do contain a request from the boss with an appeal to get it done quickly and to do it secretly, as the gift cards are to be rewards for employees. This attack was timed around the holiday season, contributing to the legitimacy of the request.
Call Centers—Target of Choice for Account Takeover Attacks
A TRUSTID survey reveals that 51% of financial service companies confirm that call centers are the vector of choice for account takeover attacks. Why are criminals targeting call centers? One reason is their authentication process. Call center representatives and customer service representatives (CSRs) often use a knowledge-based approach to authenticate customer accounts, with callers proving their identity by providing/verifying their personally identifiable information (PII).
The large-scale data breaches in recent years contribute to the account authentication process being vulnerable to attack. Millions of data troves containing PII from data breaches are available for purchase on the dark web. Additionally, criminals harvest vast amounts of PII from social media postings and other open source intelligence (OSINT). With pilfered PII, criminals can pose as customers providing CSR’s with correct answers to authentication questions. Once the CSR believes they are communicating with a valid customer, the criminal can gather more PII and execute an attack.
The ease in which criminals can fake the authentication process grabbed the attention of my colleague. She was a call center CSR, as well as, a supervisor, trainer, and quality coach. Automatic Number Identification (ANI) was part of the authentication process in use at the call center. Part of the training she received as well as provided was “trust the ANI hit.” Here’s how it works; the phone rings, the originating phone number appears on the phone console, and the computer monitor displays the name associated to the phone number. The CSR says “Hello, thank you for calling….am I speaking to (name on monitor)?” If the caller says “yes,” the CSR clicks on the linked account. As you can see all it would take for a bad actor to initiate an attack is a phone number and saying “yes.” To improve security, education is a must!
Security Through Education —The SECTF and The Human Hacking Conference
To improve security through education, SEVillage sponsors the Social Engineering Capture the Flag (SECTF) at DEF CON. This event focuses on the threat that vishing poses, allowing corporate leadership and security professionals to see how criminals could initiate an attack. No high-tech gadgets are necessary, so the ease of vishing makes it a top threat facing enterprises. All it takes is OSINT, a phone call, and knowledge of influence tactics.
At DEF CON 24, security consultants Chris Hadnagy, CEO of Social-Engineer, LLC and Michele Fincher, demonstrated how criminals use this attack vector. With the permission of CBC News’ Asha Tomilson, Fincher (posed as Tomilson) and armed herself with personal information that Tomilson posted online, skillfully used influence tactics to steer the CSR towards her goal—an account takeover. She built rapport by seeking empathy and combined it with a sense of urgency… “Can you help me? I’m getting married, and I’m stressed out.” It yielded quick results. The CSR added ‘Tomilson’s fiancé’ to the account. Finally, Fincher went in for the kill. She requested an account password reset. The customer service rep complied. Scary right? It certainly is!
SEVillage is also hosting a brand new, never-before-seen training conference called The Human Hacking Conference. This event teaches business, security, technology, and psychology professional’s techniques in human deception, body language analysis, cognitive agility, intelligence research, and security best practices. If you’re serious about learning how humans can be hacked, this conference is considered a cornerstone educational event in the security industry niche of social engineering.
Know the What, Why and How
One of the things we’ve learned from the SECTF over the past 10 years is that most employees do not understand the “what, why, and how.” What do we mean? For example, do your frontline employees know what information is valuable to criminals and why? Do they know how criminals will try to elicit information from them? For your frontline employees to be strong “front doors,” they need to be aware of the influence tactics criminals may use to manipulate them. In other words, your employees need to know what malicious social engineering looks and sounds like. And, they need to know exactly what to do if they find themselves in a potential situation.
For example, here are some behaviors from ‘customers/clients’ that should make your employees suspicious:
-
- Seeking out empathy
- Creating a sense of urgency
- Exerting pressure to make a quick decision
- Fear, e.g. “If you don’t do this for me, I’ll tell your supervisor/boss.”
Once your frontline employees have been trained to recognize malicious social engineering behaviors, the next step is to empower them.
Bolster Your Front Door Defenses Through Empowerment
Do you want your security awareness training to be effective? Then your employees must be empowered to act upon the training. That seems like a given, right? Afterall, you’ve invested time and money. Naturally, you want and expect your employees to act upon their training. However, frontline employees have a unique challenge. Theirs is a help/service culture. Whether it’s your company’s customers, clients, or the boss, they’re expected to be always friendly and accommodating—e.g. “Yes, I can do that,” “Sure, no problem.” “No” just isn’t the answer these employees will typically give.
Let’s admit it, saying “no” is scary. Why? Because it has an inherently negative connotation. Saying “yes” is socially agreeable and makes us feel good. Saying no—even to a stranger—makes us feel bad and guilty for not fulfilling their request. This is especially true for those employed with a focus on keeping customers happy. When your training says, “Always be friendly and accommodating to the customer,” how do you comfortably say “no”?
For most frontline employees, acting upon a potential malicious social engineering behavior, such as mentioned in the previous subheading, will require a new mind-set. A mindset that says it’s OK to be suspicious and it’s OK to say “no.” When company leadership supports and empowers their employees to say “no,” real progress can be made toward bolstering security posture.
Deadbolt Your Front Door
Securing your organization may feel like a hefty task and you’re right, it is. But hefty doesn’t have to mean overwhelming. There are ways to make sure your frontline feel secure and confident in their daily choices.
-
- Communication – Maintain open communication. Doing so will encourage your employees to feel comfortable reporting malicious social engineering attacks. Additionally, keep your employees in the loop. If you are expecting calls or emails that may seem out of the norm, inform them and give them the heads up. For example, I accidentally returned a new office chair my boss ordered because I was unaware of the order and suspicious of the caller asking for the delivery address. I’m still not sure if he’s forgiven me for that or not. 😉
- Clear Policies – Having clear and transparent company policies helps your frontline employees feel confident when they must make decisions on the spot. For me, knowing that I did not have permission to give out the personal information of an employee made denying the request simple. I did not have to question if I was doing the right thing or not. Laying out what information is approved for release gives your employees confidence in making decisions.
- Security Awareness Training— Having a strong and up-to-date security awareness training program that includes all employees is one of the most effective ways to secure your front door against attacks that are targeting your employees.
You can make your front door and your entire organization more secure! Know the threats facing your frontline employees and implement effective countermeasures. Train your frontline employees to recognize malicious social engineering tactics. Empower them to act on their training. And remember to keep effective communication, have clear policies, and implement security awareness training.
Lock your door kids!
Written By: Social-Engineer
Sources:
https://www.social-engineer.org/framework/general-discussion/social-engineering-defined/
https://www.social-engineer.com/lets-talk-about-social-engineering-small-businesses/
https://www.hrdive.com/news/gift-card-spear-phishing-scams-targeting-receptionists-assistants/543326/
https://www.forbes.com/sites/forbestechcouncil/2019/11/13/why-the-call-center-is-the-vector-of-choice-for-fraudsters/#165d50da6a61
https://www.social-engineer.com/equifax-breach-need-know/
https://www.forbes.com/sites/kateoflahertyuk/2019/02/12/hackers-have-just-put-620-million-online-account-details-up-for-sale-is-yours-on-the-list/#124f6af34418
https://www.social-engineer.org/newsletter/what-is-your-favorite-osint-tool/
https://www.social-engineer.org/newsletter/social-engineer-newsletter-vol-09-issue-118/
https://www.social-engineer.org/framework/attack-vectors/vishing/
https://www.defcon.org/
https://www.social-engineer.org/framework/attack-vectors/vishing/
https://www.social-engineer.com/about/
https://www.social-engineer.org/resources/7004/
https://www.social-engineer.org/newsletter/social-engineer-newsletter-volume-4-issue-51/
Image:
http://www.safetsystems.com/protect-your-home-by-thinking-like-a-thief/


Comments are closed.