The Top 5 Social Engineering Mitigation Tips
Social Engineering is still the biggest threat to corporate America. We discuss this topic a lot, so a newsletter on how to mitigate seemed appropriate.
This article comes with a caveat….. There is no way to be 100% secure from human manipulation unless you stop using humans in your business model. Since that doesn’t really work, I like to use this analogy. If you were running from a hungry bear who do want next to you, a thin, lean, fast runner or the rotund fellow who can barely walk a flight of stairs without being winded. Hate to say it, but if you want to live you will vote the later.
Social Engineering mitigation is much the same. There are definite things you can do to prepare you to run the race and not be the slowest. Make yourself unattractive and the attackers may go to the next target.
What is Mitigation?
Before I actually start defining the steps to follow for mitigation I want to define what I mean by mitigation. These steps, if followed can help a company or even individuals to prepare themselves for social engineering attacks. They can help outline best practices and even help that “when” (notice not “if”) you fall for an social engineering attack the affects are minimal.
I do not promote that there is a way to make your company impervious to social engineering, or any way to guarantee that you are 100% secure. If a company promises you that, they are lying to you.
There is not quick, 100% fix to the human OS. Being busy, emotions as well as our own personal flaws make us vulnerable and susceptible to social engineering. So with all that in mind, let me outline a few tips to social engineering mitigation that can help you when you are preparing your social engineering awareness programs.
Mitigation Tip #1: Learn to Identify Social Engineering Attacks
This first tip seems obvious, but it is amazing how many end users are not aware of the types of social engineering that exists out there. With in 8 hours of the earthquake in Haiti, the Tsunami in Japan and other such natural disasters there were scamming websites set up that promised to be able to deliver information on loved ones you may have lost.
They asked for your name, phone number, address and DOB, as well as the same info on the loved one and your relationship to them. While you waited the 3-5 days for a call back or email, you receive a phone call from a “charity” that just so happens to be asking for small donations to help with relief from the disaster you are suffering from. The person on the phone is sympathetic and has a relative also “lost” in the rumble. With quick rapport building and some fancy word smithing they are collecting your bank details for a small $20-50 donation.
Armed with that info they can easily find out, using the ABA / Routing Number, what bank you deal with. A day later a “customer service rep from calls” asking you to verify a payment to a charity you made. The praise you for your generosity in helping those poor souls and they have your routing, account and amount details so it must be real, right? All they need is your social security number to verify your account.
With in 2-3 days the scammers have all your personal details, your banking details and your SS number, and with that your identity is stolen.
Why is this information important? Without knowing that people are out there doing this opens you for attack and a greater potential of falling for this vector. But if employees and individuals spend some time becoming educated on what is going on, they will be made more aware and watchful of potential threats.
This can seem like a daunting task, after all where does one go? How do you find info? We all have jobs and lives and finding the information needed can seem like another full time job.
We work hard to compile the vectors found and being used on social-engineer.org. There are other websites like exploit-db.com that will list public exploits, white papers and other helpful pieces of info that can make it easier for a person to be made aware of what is going on in the SE world.
I usually suggest to companies to try and compile a monthly newsletter for their employees that will make the job for them easier and will motivate them to take this first step seriously.
Mitigation Tip #2: Be Aware of the Value of the Information You Have
This next tip is a hard one to really define, but let me start off using an illustration. In your home you probably have things of varying value. You might have dishes that are for every day use, then your wife may have the “special dishes”, ones that are in a special cabinet and used only on certain occasions.
You have been told that those dishes are more valuable, are special and should not be used or handled the same as the other dishes. The same goes for information and data. There is much information you have at your company that is public, that needs to be talked about and that can be freely given. Then there are sets of data that need to be handled with more care.
Even with the data that is public we must train ourselves to think critically and ask ourselves, “Does the person requesting this information deserve to be given it?”
This is not a question of arrogance, as much as it is a question of right. If a person calls that says they are an upset customer. During the process of the call you are talking with them and they begin to ask questions like “Who handles your trash removal?” or “What vendor do you use for ?” Our critical thinking centers should kick in and say “Hey this information is out of line with the conversation and this MAY be a social engineering attempt.”
Keep in mind that small, innocuous pieces of information can cause some of the biggest breaches. In the case of Sony, before 10’s of millions of credit cards where released in the wild, there was just a few cleverly placed phone calls that helped the attackers piece together the SQL string needed to launch that massive attack.
Gone are the days of “whats your password?” and now attackers are launching smaller but more frequent attacks that will help them piece together the puzzle they need to launch a successful attack vector.
This may seem obvious, but it is amazing how hard this is for large corporations. 10 years ago your company purchased a system that required Internet Explorer 6 and as the years passed many people got used to using it and the cost of upgrading was too high. What are the real costs though?
According to research done by SecurityFocus notice the chart below:
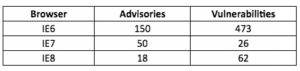
In Defcon 18’s Social Engineering CTF we found that a large majority of the companies where still using IE6 and many were still using IE7 in Fortune 500 Companies. That means an attacker has 499 opportunities to exploit a person just on the browser alone.
That doesn’t include the many that admitted to still using Adobe Reader 6, 7 or 8 or other key pieces of software that are full of security vulnerabilities.
The sad fact is there is no way to 100% guarantee that your people will be secure. Knowing that at some point your people may fall victim to an SE attack makes this mitigation point ever more important. If an attacker can convince an employee to visit a malicious webpage or except a malicious file we can at least rest assure that if we are not using vulnerable software we are not the “low hanging fruit”.
This is not to say it is an easy process, getting approvals, budget and man power to handle upgrades on a large scale can be a daunting task. I am well aware of how difficult this can be, but I urge you to really ask yourself or your management this one question:
“Which will cost less, upgrading or breach?”
The latest report from Symantec puts the average cost of a breach at $7.2 million dollars. That astounding number should sober up any CFO into approving upgrades to critical systems that hold vulnerabilities.
Mitigation Tip #4: Developing Scripts
Nothing irritates me more than when you call your provider because there was a problem on the bill or with the service. After you get done laying out your case and complaining about the lack of service, nothing gets resolved, you spent about 60 mins on hold and you are about to hang up frustrated and the service rep says, “Thank you for calling I hope I was of service to you, have a great day.”
I can feel my blood boiling now and I am just talking about it. Why do customer service people do that? They are given scripts and they follow them to the letter and even when the sentence makes little to no sense, they are in such a routine they just say the script anyway.
As a side note, want to see a human buffer overflow in action? Next time you have call your cell phone or credit card company before they ask say, “Sure you can record this call” and when she gets to that point notice how half way through reading the script she can’t process that you already answered what she is asking. Its hours of family fun.
Anyhow, back to the point – I am NOT speaking about these types of scripts. I am talking about the concepts of a script. Let me explain.
Why is it that people will take a martial arts class? Of course there are the self defense, health, exercise aspects of it. But in the end, it is to train your body and mind to react a certain way when in a certain circumstance. If some one comes at you, when trained you will react much differently that if untrained.
This is a type of mental scripting. If person comes at you with closed fist, first move left, then retaliate with a throw, punch or kick.
The same way, is what I suggest here for social engineering attacks. Script out the potential attacks against you, your people and company. Then determine what is the best course of defense and then educate yourself and staff to react that way.
If a phishing email comes in do not just click delete, but the script says to first analyze the email, forward it to your abuse, tech or privacy team and report it to your team members and manager so others can be alerted. This type of 1-2 punch can level the playing field and create an environment of security.
The problem is that many of the scripts are written in the form of “policy” and that dirty word doesn’t help anyone be more secure. I am not saying that policy is a waste of time, but that more is needed to create this environment.
Just like in that martial arts class you don’t read the book and go to one class and you are a black belt. More is needed, weekly or at times daily practice will train your body and mind to react a certain way.
It is the same with security, frequent practice sessions, drills, tests and educational opportunities can help you create these mental scripts so your body and mind will react the right way when a real attack comes.
The goal is to train yourself, whether at work or not, to be a critical thinker and to see a situation that may poise a threat to your security and react in a way that helps raise the shields and ward off any potential attack.
Each script should contain a few stages:
- Analysis
- Action
- Reaction
For example, you are sitting in your cube at work and an email comes in.
A script would say:
1. Analysis: Did you expect a package? Is the USPS known for sending ZIP files? If they do, would it be to “customer” or your name? Notice the urgency. Too much is wrong here.
2. Action: Don’t be too hasty to just delete this email. Forward it to the proper people with in the company to handle this matter. But whatever you do – DO NOT OPEN THAT ZIP.
3. Reaction: Don’t be a hermit with this information. Share it with co-workers (no, not the email) but the information can be spread so others know this scam is going around.
Having this script mentally (or even physically) written out can save you from a lot of headache and a breach.
Mitigation Tip #5: Receive, Learn and Act upon Social Engineering Pentests
I know we hear this analogy a lot in this field, but it is important to use. We are told it is good to get check ups with our doctor. We don’t go just when we are feeling bad and sick, but also when to routinely have things checked out to avoid serious problems. After a certain age we might even go once or twice a year just to make sure everything is working the way it should. Why?
The risks of not catching certain sicknesses early can mean our death or other serious problems.
Our company’s health is no different. Relying on our internal IT staff to do that check up is as silly as saying you can do your own check ups and don’t need a doctor. Why? It is not because they are incompetent or not smart enough, not at all. It is cause they are too close to “home” and may not look in the right spot or check the right thing to find that potential problem.
A good quality penetration tester is like a skilled doctor. This topic alone can be another whole article, but it is important when choosing a pentester to not just go with the cheapest deal around.
Sure, as a pentester it is fun to “break into things” and it is exciting to find a vulnerability to report, let’s not lie about it. But if that is where your pentester stops you are being cheated.
That would be no different than the doctor walking in to the office after your exam and saying, “Well we found a huge lump here. Have a nice day.”
You want that doctor to give you the next steps, what do you do? How do you do it? How do you fix it? Why should a pentest be any different? After you get the report and gaping holes are exposed it is a crime to leave the company and not help with at least ideas on how they can mitigate.
As fun as the “breaking part” is of the pentest sometimes we need to be reminded that we are the good guys and as such, our goal should be to help the client to fix the problems.
Ok. I am off my soap box, this mitigation step is about you and how to learn from these tests. After you chose the right vendor the worst thing you can do is ignore their help. It would be like seeing a great doctor, he tells you that they found this lump, tells you what tests are needed and what action is needed to fix it and live and you just walk out of the office and ignore everything he said.
It is imperative to take action and to heed the warnings and fix the problems that exist. Not doing so can lead to a breach and it is also a huge waste of your time and money to do testing but ignore the results.
Many times, doctors will tell us that to avoid the serious problems there are preemptive measures we can take to avoid health issues. Exercise, diet, daily routine are all important.
The same is with our security. There are preemptive measures we can take to save us form serious breaches. Take the time to invest in frequent security awareness courses and training. Now I don’t mean those cheap 45-60 minute dvd’s that get passed around your company. Personally, when I work with my clients I set up times to go out to their location and run live security awareness sessions. I do small doses of a couple hours a piece that help their employees realize the dangers that exist and how to combat them.
Combine good quality security awareness with periodic pentests through out the year and what you create is an environment that breeds security.
Is That All?
Is what I am saying then that by following these 5 tips you can be guaranteed the remain breach free and un-hacked? Not at all. These five tips are to help create a security minded company that is not the low hanging fruit. Times used to be that I would say, “if you get hacked” now I say “when you get hacked”. It is more likely that every company will experience some breach in the future if not already.
How much loss there is, how much it costs and how long it takes to fix it are all dependent on you. Take the right actions now to create a secure environment.
Social Engineering is the easiest way into a company, it is still valid, still used and still very dangerous – but it is not forced by compliance or government agencies to be tested for. Don’t wait to be breached to take this seriously, don’t become one of the statistics for 2012, instead take action now. Be decisive and stay secure.
Written by: Chris Hadnagy

