Social-Engineering In The News
It is not everyday that social engineering stories make the news. When we see some that stand out, we want to write about them. We recently saw three stories that stood out as pure social engineering in action. Let’s take a few moments to analyze each.
Flashback Trojan
By now, most of you have probably heard about the Flashback trojan that quickly spread and infected over 600,000 Mac computers running OSX. The original Flashback trojan, released in September 2011, masqueraded as a Flash installer served up by malicious websites. Safari users who had their browser settings set to auto-open “safe” files were shown a desktop installer just like they would if they were installing a legitimate copy of Flash. The newest infections, caused by Flashback, are served up via drive-by downloading. A drive-by download is a nefarious bit of code that is unknowingly sent to a user when they visit a website, open an email, or click on a pop-up. The malicious code is sent to the user’s computer completely invisible to the user by exploiting ActiveX or, in this case, Java.
After installation, the trojan goes to work disabling firewalls and anti-virus software and reports back to home base as “ready to go”. The software, now installed, allows attackers to remotely control your computer turning your computer into a member of their botnet; ready to attack internet resources, spam email, or attack other machines.
Drive-by downloads are becoming increasingly more prevalent and a perfect way for an attacker to compromise your systems. Phishing emails are sent out every day by hackers looking to snag something on their lure. We recently received word from a professional penetration tester that during his most recent phishing attempt, he received a 100% click rate! A good social engineer can tailor things in a way that they are very difficult to spot and thus, hard to defend against.
In addition to this obvious attack vector, there is another massive social engineering side to this story. That is what Apple has done to convince its loyal fans and customers about how safe they are.
Notice the message on the Apple website… “It doesn’t get PC viruses.” The language that is used by Apple implies that Macs are more secure, impervious to the plague that is Windows based viruses.
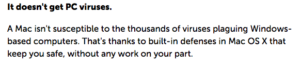
Apple customers believe this to the extent that they felt safer clicking links and allow programs to run, to the tune of over 600,000 being exploited.
Czech Social Engineers Steal a Bridge
In the town of Slavkov, Czechoslovakia, a gang of social engineers arrived at the train station one morning posing as construction workers. The gang approached the depot personnel with work orders to demolish the steel footbridge that went over the tracks as well as a portion of railway track supposedly to make room for a cycle path. Apparently, the documents and the story were official enough that depot personnel approved the work order and the gang began work dismantling the bridge.
One Russian newspaper stated that a group of police stopped the thieves and when the men presented their forged paperwork, the police left them alone. The paperwork looked legit and seemed to be in order.
Only after the bridge and tracks had been fully dismantled and hauled away did anyone from the rail station bother to verify the authenticity of the documentation along with the story told. Imagine their surprise when they learned there was no such work order to demolish the bridge and that thieves just stole a bridge right under their noses! It is estimated to cost millions of dollars in steel to rebuild the bridge.
Forged documentation is one of the social engineer’s favorite tools and depending on the quality of the forgery, can yield devastating results. With a simple badge printing tool, found easily on the Internet, combined with the plethora of employee badges that can be found scattered about Facebook, Flickr, and Twitter, forged documents can go a long way. At last year’s Social Engineering Capture the Flag event, at least two contestants discovered badges that clearly identified every piece of information an attacker would need to duplicate the badge.
Social Engineer Obtains Paul Allen’s Debit Card
In other SE news, an Army deserter, Brandon Price of Pittsburg, PA successfully convinced Citibank that he was Paul Allen (YES, *the* Paul Allen) and had Citibank change Allen’s address to Price’s, then UPS overnight Brandon Price a new card. Let’s say that again… an Army deserter used social engineering to take over the debit card of one of the richest men on the planet. Paul Allen is worth over 14 billion dollars, owns the Seahawks and the Trailblazers, and an average citizen was able to have his debit card over-nighted to him.
How? One report states: “An individual identifying himself as Paul Allen called the customer service department of Citibank. The caller stated that he had misplaced his debit card at his residence, but did not want to report it stolen. The individual then successfully ordered a new debit card on the account of Paul Allen and had it sent via UPS,” FBI agent Joseph J Ondercin explained in a criminal complaint.
Read that again. Basically, he just called in, identified himself as one of the richest people on earth, and ordered a new debit card to HIS address.
This brings up some serious privacy concerns. If the debit card of an individual, such as Paul Allen, can be commandeered, imagine what can happen to Joe the Plumber’s accounts. This also illustrates how effective and potentially devastating the social engineering attack can be. As the “cost of doing business” goes up for criminals, the use of social engineering increases because of its low barrier for entry. With the advent of VOIP, phone calls today are virtually free. A good social engineer can take over a billionaire’s account for free. Without spending any money on equipment, travel, training, etc., the social engineer can strike with catastrophic results.
Mitigation
Here we were going to list some ways to mitigate these threats, but we decided to post a link to Chris’s RSA speech entitled, 6 Ways To Mitigate SE that will show you everything you need to know. Chris’ RSA Speech.
In addition, you can join Chris and crew in the next two installments of an in depth webinar on that topic with Core Security.
Thanks to worldwide exposure given to the danger of social engineering by events like the Social Engineering Capture the Flag contest held at Defcon 18, Defcon 19, and again this year at Defcon 20, companies are beginning to see how vulnerable they really are to social engineering attacks. Only through live, personalized, real-world social engineering training, audits, and penetration testing can companies hope to combat this ever growing threat. Until companies start taking social engineering seriously, we will continue to see headline making reports such as these coming through.
Written by: Eric “Urbal” Maxwell
Sources:
https://www.zdnet.com/article/over-600000-macs-infected-with-flashback-trojan/
https://www.nbcmiami.com/news/weird/NATL-Czech-Bridge-Footbridge-Heist-Railroad-Track-Stolen-Thieves-149475535.html
https://www.computerworld.com/article/2502247/microsoft-co-founder-paul-allen-victim-of-id-theft.html
https://www.social-engineer.org/framework/general-discussion/categories-social-engineers/penetration-testers/

