Social engineering. We can remember a time when typing that into a search engine lead to almost no return. Maybe some “free burger” videos or the like, but nothing about security. Jump forward to the present day and social engineering is more than just “free burgers”, it is a vector used in over 66% of all attacks by hackers, hacktivists and nation states.
For the last five years, Social-Engineer.Org has provided free education in the form of podcasts, newsletters, blogs and reports. The five books that Chris has written has lead to our company being engaged by organizations from all industries in the US with the goal of uncovering, patching and mitigating social engineering vectors.
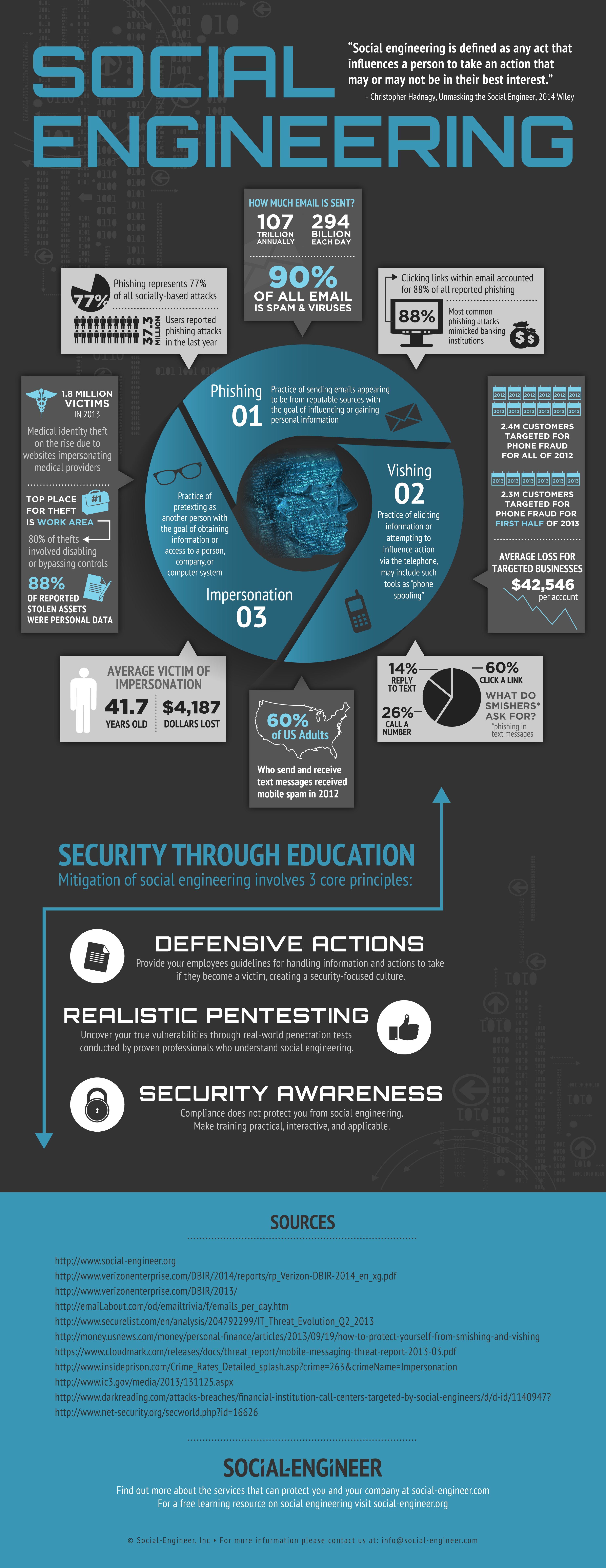
We have compiled statistics from our many engagements over the years, such as:
- 90% of the people we ask will provide not just the spelling of their names but their email addresses without confirming our identity
- 67% of the people we ask will give out social security numbers, birth dates or employee numbers
- We have a 100% success ratio in physical breaches
How do these numbers compare to the market around the globe? That is why Social-Engineer decided to fund the creation of an intensive and extensive infographic. Research has been compiled from all of the latest reports and statistics available and put into a graphical format to help educate people on these threats.
As always, our motto is “Security Through Education” and we wanted to make the infographic about that, so it is complete with three principles to help you, your families, and your companies stay protected from social engineering threats.
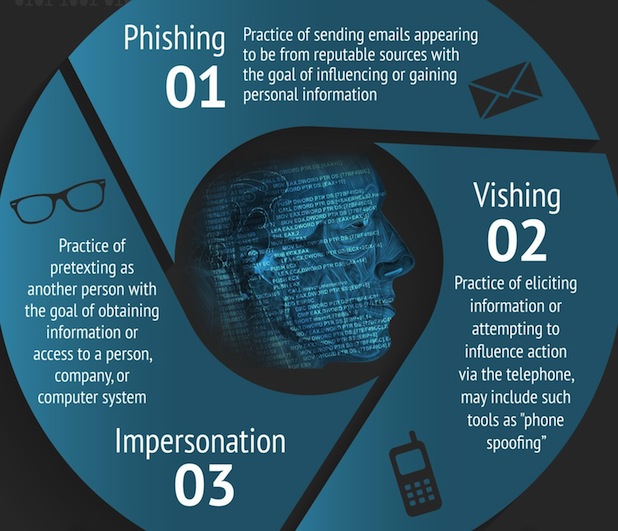
We hope you enjoy it and find it extremely useful. Please take a quick look, and if you like it, pass it on to someone you know. Human-based attacks in the form of phishing, vishing, and impersonation are on the rise. If you follow our Twitter (@SocEngineerInc, @humanhacker), you’ll see the stories. Remember, technology won’t keep you safe.
We hope you enjoy the info graphic below. It is also in our resources page.
3 Comments
Comments are closed.


Hi….
Unfortunately one of the biggest spoofs going I.e. phishing is job applications. When your desperate you don’t take the precautions that, truthfully, you shouldn’t have to do. Does it constitute fraud and sorry about your luck. Oh well when you are on your last dime it doesn’t matter anyway. Zero minus zero still equals zero. .
When I initially commented I clicked the “Notify me when new comments are added” checkbox and now each time
a comment is added I get several emails with the same comment.
Is there any way you can remove me from that service?
Thanks!
As mentioned in the blog, Phishing and Vishing are on the rise. Here are some ways to stay protected from such attacks:
• Avoid using mails for confidential purposes.
• Don’t post too much personal information online.
• Be Aware of your surroundings
• If you find the email suspicious, verify the mail with the sender right away.
• Be suspicious of all unknown callers
• Don’t trust caller ID
• Ask questions
• Register your number with DND Service.