Why Attackers Might Use Social Engineering
Attackers use social engineering tactics because they work. Indeed, there is no patch for an users without adequate training. Or, even a security professional who forgets to follow what they know.
Social Engineering is the Path of Least Resistance
Malicious actors know it could take hours, weeks, or even months to successfully brute force their way into a network to steal credentials. However, with social engineering tactics, those very same credentials can be stolen in just a matter of minutes. For example, all it takes is the right pretext and a phone call, or email. Additionally, an attacker might try to gain physical access to a company’s network computers as well. To accomplish this an attacker might impersonate a delivery person, construction worker, or tech support. Sifting through open source information, dumpster diving, or talking with a disgruntled employee, may yield information that is used to gain illegal access. Once the attacker is inside, a common USB thumb drive is all that’s needed to infect a computer. Thereby gaining access to the network.
The role played by social engineering becomes greater as software products become more secure as well as harder to crack. Therefore, to protect yourself successfully from these attacks you must first, understand what tactics a social engineer use. Second, how they will use them. And lastly, what methodology they will employ in their attack cycle.
Social Engineering Attacks On The Rise
The incidents of social engineering tactics used in cases of fraud and data breaches continue to increase. Reports released by industry leaders such as Agari, Symantec, and Verizon Enterprises indicate that social engineering tactics (phishing, vishing, and impersonation) are being used in conjunction with digital hacking methods to make attacks more effective and inevitability more profitable for the attackers. According to the 2020 Verizon Data Breach Investigations Report, 22% of confirmed breaches involved Social attacks.
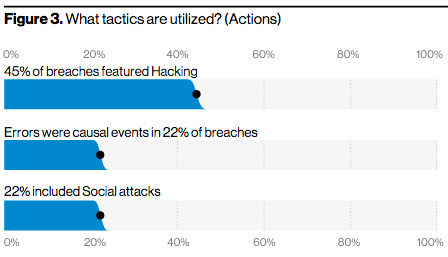
Screenshot from 2020 Verizon Data Breach Investigations Report
Phishing Examples
- City treasurer was victim of a phishing scam, transferred $100K to phoney supplier
- ‘Easier Than Robbing A Bank:’ City of Chicago Almost Lost More Than $1 Million In #Phishing Scam
- The Nasty List #Phishing Scam is Sweeping Through Instagram
Vishing Examples
- Victims losing an average of $164K to scam that targets Chinese Americans
- 24 Charged In Medical Supply Phone Scam Costing Medicare $1.2 Billion
- Mumbai garment shop owner duped of ₹30K
Impersonation Examples
- Man Posing as Construction Worker Steals $15K in Laptops at Memorial Sloan Kettering
- Oklahoma Walmart Robbed by Man Posing as Armored Car Employee
- Man Impersonates Pest Control Worker to Enter Commercial Building
Social Engineering — a Common Element of Malicious Attackers
Social engineering is a common element of malicious attackers. As this framework outlines, malicious social engineers have many tools in their arsenal. And many attack vectors at their fingertips. Attackers know that most employees do not realize they are doing something wrong; and/or do not understand the value of the information they are disclosing. It is this naivety that creates a perfect atmosphere for a breach. The only way to protect against these attacks, is to create a security-minded culture within your business or organization through continual education as well as training.

