The Attack Cycle
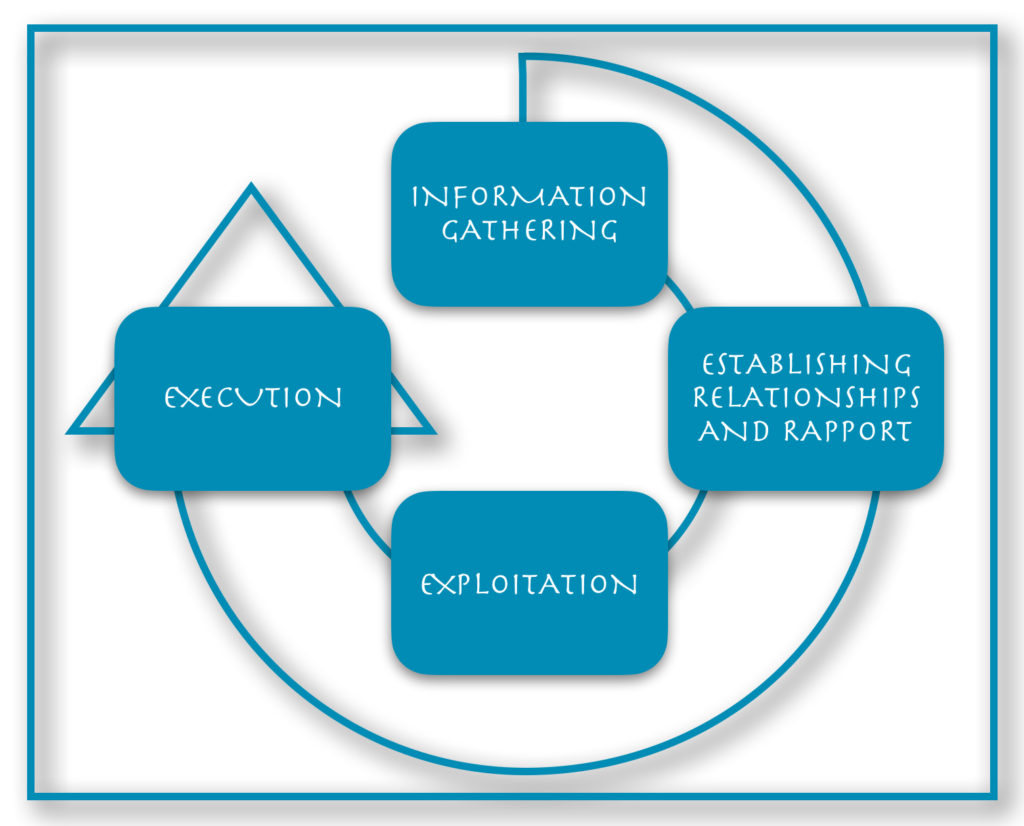
There is a predictable four-step sequence to social engineering attacks, typically referred to as the attack cycle. It includes the following: information gathering, establishing relationship and rapport, exploitation, and execution.
However, a number of factors may cause the attack cycle to repeat several or all of the stages for any given target. For example, an attacker may use a series of attacks to work their way to the target because going straight to the intended recipient would likely fail. Depending on the nature of the attack and the target, the cycle can repeat several steps. It may even go through every step multiple times. This is also known as a privilege escalation attack, making use of previously gained familiarity/referral from within the target company or exploiting information gained from previous interactions.
1. Information Gathering
The likelihood of success for most attacks depends on this phase, so it is only natural that attackers invest the majority of their time and attention here. Information-gathering techniques are elaborated on in the Framework. With the right information, the attacker can determine the attack vector, possible passwords, likely responses from individuals, and refine goals. At this phase, the attacker becomes familiar and comfortable with the target and formulates a strong pretext(s).
2. Establish Relationship and Rapport
This phase establishes a working relationship with the target. This is a critical point, as the quality of the relationship determines the level of cooperation and extent to which the target will go to help the attacker accomplish the goal. It can be as brief as hurrying towards the door with a big smile and eye contact so the target holds the door open for the attacker to walk through. Or it could be connecting on a personal level over the phone or as personal as showing family pictures and sharing stories with the receptionist in the lobby. It can also be as extensive as building an online relationship with the target through a fake profile on a dating or social networking site. Creating rapport is covered more in-depth in the Framework.
3. Exploitation
This is when the attacker uses both information and relationships to actively infiltrate the target. In this phase, the attacker focuses on maintaining the momentum of compliance established in phase 2 without raising suspicion. Exploitation can take place through the divulging of seemingly unimportant information or access granted/transferred to the attacker. Examples of successful exploitation include:
- The act of holding the door open or otherwise allowing the attacker inside the facilities
- Disclosing password and username over the phone
- Offering social proof by introducing the SE to other company personnel
- Inserting a USB flash drive with a malicious payload to a company computer
- Opening an infected email attachment
- Exposing trade secrets in a discussion with a supposed “peer”
4. Execution
This phase is when the attacker achieves their ultimate goal, or for various reasons the attack ends in a way that avoids suspicion. Generally, an attack ends before the target begins to question what is happening. Instead, the attacker ends with the target feeling like they did something good for someone else, ensuring possible future interactions to continue. In addition, the attacker erases digital footprints and ensures no items or information are left behind. As a result, the attacker accomplishes two important goals. First, the target does not know an attack took place. Second, the attacker keeps his identity hidden. A well-planned and smooth exit strategy is the attacker’s goal and final act in the attack.
(Contributor: Amade Nyirak)
Image: www.social-engineer.org