Hackers
The word hackers originally described extremely skilled people who would push the limits of computer systems. There was no need to define hackers as white, black, or grey. However, in time the word hackers took on negative connotations. As a result, the word hacker embraces multiple meanings. For example, Merriam Webster, provides these two definitions: 1.) a hacker may be an expert at programming and solving problems with a computer 2.) a person who illegally gains access to and sometimes tampers with information in a computer system. The security community now generally recognizes three overarching types of hackers: ‘black hat’, ‘grey hat’, and ‘white hat’. These labels can also be seen on a sliding scale. Hackers, however, typically identify with one category on a day-to-day basis. We’ll break down the hat colors for you. For additional information on hacking and how to enter the field, please see this Newsletter.
Black Hat
The black-hat hacker has hostile intent and is willing to engage in illegal activity. Labeling them as “hackers,” is a misnomer. Since they do not have permission to hack from the owning entity they are “cyber criminals”. Therefore, within the framework we refer to black hat hackers as cyber criminals. They may be a lone amateur, an underground organization, or a collective working under a nation-state. They may be highly proficient in their knowledge of computers, hardware, software, and networks. Additionally, they may also write malware and may be adept at bypassing both protocols and people.
Their goal usually is to steal login credentials, financial data, and personal information. They may also seek to deceive people and systems, deny or disrupt services, and modify or destroy data. Money is the motivator for most. According to the 2022 Verizon Data Breach Investigations Report (DBIR) 96% of data breaches had a financial or personal gain motive. Thrill-seeking also plays a part, as do strong beliefs and sometimes, direct orders. Next, there is the grey-hat hacker.
Grey Hat
The grey-hat hacker looks for weaknesses and vulnerabilities without approval or permission. Once this hacker finds an issue, they’ll typically report it and sometimes request a fee to fix the issue. If the owning entity doesn’t agree to pay, or refuses to acknowledge or address the issue themselves, the grey-hat hacker may post the vulnerability publicly online for all the world to see and potentially exploit maliciously. Since they did not receive permission to act in the first place, their activity is usually considered illegal.
White Hat
White-hat hackers are security experts also known as ethical hackers, or penetration testers. White-hat hackers will often use similar hacking methods as black and grey hats. Albeit, with one very important exception—they have permission to hack. As is the work Social-Engineer, LLC performs for its clients, the white-hat hacker’s actions are 100% legal. Organizations hire them to test security systems, perform penetration tests, execute vulnerability assessments, run phishing campaigns, and more.
Human Hackers
Within security there has been a growing trend to study how criminals use social engineering to target people within an organization rather than implement a technical attack. This led to another discipline within hacking that focuses on human vulnerabilities in addition to system vulnerabilities—human hackers. Some of these human hackers are white-hat hackers who study and implement social engineering techniques. As discussed in this Framework, there is a predictable four-step sequence to a malicious social engineering attack typically referred to as an attack cycle. It includes the following:
- information gathering,
- establishing relationships and rapport,
- exploitation and
- execution.
Human hackers use their knowledge of the above-mentioned malicious social engineering attack cycle to raise awareness of an enterprise’s vulnerability. The training and education provided in such services as, Managed Phishing Service, Managed Vishing Service, and the Social Engineering Security Assessments, equip people within an enterprise to be its front-line defense against malicious social engineering attacks. You can learn more about human hacking by attending the Human Behavior Conference.
Benefits from Ethical Hackers
The software industry is just one sector that benefits from the skills of ethical hackers. For instance, during 2018, ethical hackers found software vulnerabilities that averted crises in ten major companies.
Government agencies as well as corporate industries have taken note of the white-hat hacker programs’ success and benefits. The Pentagon now routinely runs bug bounty programs to strengthen its security posture. During the September 3-18, 2019, Hack the Proxy program, the Pentagon gave 81 ethical hackers from around the world access to probe the department’s Virtual Private Networks (VPN), virtual desktops, and proxies. The Pentagon released its results on October 14, 2019. The ethical hackers discovered 31 vulnerabilities; nine considered high severity, and 21 with medium/low severity.
Why Criminals use Social Engineering Techniques
Cyber criminals often use social engineering techniques because humans are much easier to hack than network vulnerabilities. Malicious social engineering is recognized as one of the greatest risks to information security. In fact, the 2022 Verizon Data Breach Investigation Report (DBIR) confirms that criminals actively target human weaknesses. For example, according to the DBIR, 82% of breaches involve the human element. In a social attack, criminals target emotions such as fear, urgency, or obedience to influence decision making. The compromise of the individual is not the ultimate goal, but rather serves as the launching pad. After obtaining personal information, passwords, remote user accounts and more, the malicious actor will then use this information to launch an attack on the target—i.e., company or organization. The results can literally devastate a company or organization in a matter of minutes.
Criminal Hacking Groups
According to the 2022 Verizon DBIR, hacking attempts to intentionally access or harm information assets without authorization continue to play an active role in data breaches. Listed below is an example of a criminal hacking collective.
The Dark Overlord
The Dark Overlord is a criminal hacking collective that claims responsibility for the database breaches of numerous entities. They initially appeared to focus on medical facilities. As reported by Motherboard, the cybercriminal(s) broadened their focus and targeted the family run business, GorillaGlue, stealing 500 GB of research and development materials.
They then set their sights for Hollywood. According to Variety, the cyber criminals(s) breached Larson Studios , a Hollywood-based audio post-production company and stole titles of numerous movies and TV shows from major studios such as, Netflix, ABC, CBS and Disney. The malicious actors demanded a ransom of $50,000 from Larson Studios. Although Larson Studios paid the ransom, the cyber criminals released the popular Netflix show, ‘Orange is the New Black’, to a piracy network. It appears that in the case of Larson studios, two vulnerabilities provided the opening the cyber criminals needed. First, their employees were not sufficiently educated in the importance of computer security. Secondly, not all of their computers had been updated. ‘Orange is the New Black’ episodes were on servers running Windows 7. The malicious actors got in and the data got out.
State Sponsored Hackers
State sponsored hacking is dominating the headlines. Whether it’s meddling in elections, global ransomware attacks or Distributed Denial of Service (DDoS) attacks. These examples from recent news articles show how devastating the consequences can be.
The Lazarus Group
The Lazarus Group also known as Hidden Cobra are cyber actors of the North Korean government. They are one of the most destructive hacking collectives on the Internet. The Lazarus Group is responsible for the devastating 2014 Sony hack, the 2017 Wannacry ransomware attack, multiple DDoS attacks, and the disappearance of over $571 million in cryptocurrency.
On February 4, 2016, The Lazarus Group allegedly committed what may be one of the largest and most brazen bank heists in history. The hacking collective breached Bangladesh Bank’s systems and stole its credentials for payment transfers. Reports indicate that the FBI suspect that the malicious actors may have had inside assistance from bank employee(s). With the payment transfer credentials, the cyber criminals masqueraded as Bangladeshi bank officials and flooded the Federal Reserve Bank of New York with fraudulent money transfer requests totaling $101 million USD. A simple typo held up a transfer request for $20 million USD and raised the alarms. In the end the hacking collective got away with $81 Million USD.
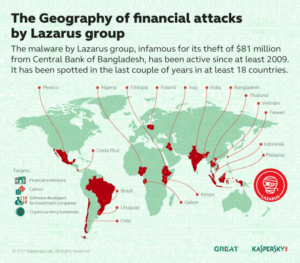
The Lazarus Group is suspected to be behind the $100 million altcoin theft from Harmony Horizon Bridge in June 2022.
Fancy Bear
Fancy Bear also known as APT28, Pawn Storm, Sofacy Group, Sednit and STRONTIUM) is a cyber espionage group and is associated with the Russian military intelligence agency. Their hacking methods include zero-days, spear phishing, OAuth phishing, and malware. They are alleged to be behind numerous breaches including the 2016 attacks on the World Anti-Doping Agency (WADA) as well as the spear phishing attacks that led to the breach of the Democratic National Committee (DNC). As reported in the Business Insider, 2017 saw Fancy Bear notably increase the sophistication of its cyber-attack with the OAuth phishing campaign that targeted France’s centrist presidential candidate, Emmanuel Macron.
Fancy Bear surfaced again in the news in 2022 in connection with the war in Ukraine. According to Ukrainian cybersecurity officials, Fancy Bear is behind a new wave of malware attacks being spread via innocuous-looking emails.

