Typical Goals
The typical goals of a malicious social engineer are comparable to the goals of the average person in the work force. For instance, knowledge is power, the more you know, the easier it may be to succeed. A malicious social engineer has some of the same typical goals that an average person may have but, with one difference, ethics.
Ethics
Ethics are the base standards of what is good and bad within a society. For example, if society as a whole views a behavior as bad, laws are made to punish the behavior. Indeed, ethics are what separates the money making goals of the average person from the malicious social engineer; out to make their money or their name by stealing knowledge and using it in a non-ethical way.
Typical Goals
Dr. Max Kilger, co-author of the Honeynet Project, identifies six motivatiors for non-ethical computer activity. These motivators also apply to social engineering. The six motivators are: money, entertainment, ego, cause, entrance into a social group, and status within that social group. Slides 80-87 in this presentation touch on this.
These motivations are similar in any society. For example, people want to make more money or get into a social group. It is important to note that Dr. Kilger did not include some key motivations: knowledge, revenge and curiosity. Each of these motivators are also a goal of social engineering. The ultimate goal, is information. Information that satisfies the aforementioned motivators. Below are social engineering attacks that highlight some of these motivators:
- Money
City of Ottawa treasurer fell victim to US$100K phishing scam - Cause
Egyptian activists targeted in phishing scams - Entertainment
Someone hacked printers worldwide, urging people to subscribe to PewDiePie - Knowledge
Phishing Continues to Get More Sophisticated - Ego
Mirai Botnet Behind Massive DDoS Attack Against Dyn DNS
Source Code For loT Mirai Botnet Released - Revenge
Sacked IT guy annihilates 23 of his ex-employer’s AWS servers
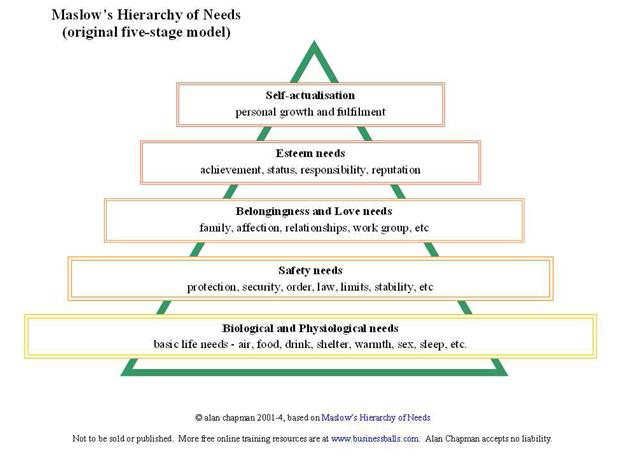
Maslow’s Hierarchy of Needs
Figure 1 depicts the basic needs to survive at the bottom of the triangle. Esteem needs and self-actualization are at the top of the hierarchy. Although the original diagram has been updated; the researcher chose to include the diagram from the 1970’s since it includes the cognitive need of knowledge, a main motivator for criminal behavior.
Using this hierarchy, you can see that the base of the pyramid is the most primal of needs. The need for food and drink. Indeed, the basic life needs often cost some amount of money, which may be gained by social engineering. In fact, each of the goals and motivators could be placed into the hierarchy of needs. Although some needs may hold different positions for the social engineer. Self-actualization; or ego, esteem, status and cause, can be found at the top, or close to the top of the pyramid. A key motivator often times can be the need for recognition.
Social Engineering as a Protection
On the other hand, social engineering has become essential to executing professional penetration tests. A security professional may use the very same tactics as a malicious social engineer, but with one MAJOR difference; motivation. The motivation for the professional social engineer is to help a company see the dangers that lurk in the business world and what they need to do to increase their security. Simulated attacks during a pen test are an effective way to assess vulnerabilities. It enables a company to see clearly what they are doing correctly. And where to make improvement. Additionally, companies now have actionable data to implement specific training and education. Indeed, employee education and training can make the difference between success and failure in a social engineering attack.
Some examples of professional social engineers:
Conclusion
The goals of a malicious social engineer are comparable to the goals of any criminal activity. For instance, knowledge, power, money, control, bragging rights, and etc. Malicious social engineering with the purpose of data theft, is like any other crime, it contains motive and a goal. If computer security personnel can brainstorm the reasons a social engineer might want to enter their system, along with a list of possible goals of that engineer, then preventative measures and training can be implemented.